WebSome of these disadvantages are mentioned below: 1. In this article, we will explore some alternatives and options that use Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) instead of ICMP. As different types of errors can exist in the network layer, so ICMP can be used to report these errors and to debug those errors. For example, you may use ICMP to check the basic connectivity and availability of a host, TCP to check the performance and functionality of a specific service or application, and UDP to check the bandwidth and quality of service of a network path. 
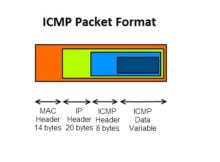 ICMP packets are IP packets with ICMP in the IP data portion. Therefore, network operators need to ensure that their network devices and policies support ICMP for BGP keepalive messages, and that they are consistent across the AS. Practically, ICMP offers error control and often it is employed to report errors, send management queries and operations information.
ICMP packets are IP packets with ICMP in the IP data portion. Therefore, network operators need to ensure that their network devices and policies support ICMP for BGP keepalive messages, and that they are consistent across the AS. Practically, ICMP offers error control and often it is employed to report errors, send management queries and operations information. 
 Network devices like routers need to use the ICMP in order to send the error messages. Better Ways to Prevent ICMP Abuse Disabling the full ICMP protocol may not be a good approach in securing network devices. Find out why Martello is Microsofts go-to-solution for Microsoft Office 365 Monitoring >>, Microsoft Teams call quality issues can stem from a lot of places. If youve ever used the Ping or Tracert command, youve taken advantage of the Internet Control Message Protocol (ICMP). ICMP creates and sends messages to the source IP address indicating that a gateway to the Internet, service or host cannot be reached for packet delivery. Within each message type, there are several codes to identify a specific condition or request. Consequently, it is quite accurate when it comes to selecting the most suited approach. Organizations can use the iPadOS Files app to manage files locally or in the cloud.
Network devices like routers need to use the ICMP in order to send the error messages. Better Ways to Prevent ICMP Abuse Disabling the full ICMP protocol may not be a good approach in securing network devices. Find out why Martello is Microsofts go-to-solution for Microsoft Office 365 Monitoring >>, Microsoft Teams call quality issues can stem from a lot of places. If youve ever used the Ping or Tracert command, youve taken advantage of the Internet Control Message Protocol (ICMP). ICMP creates and sends messages to the source IP address indicating that a gateway to the Internet, service or host cannot be reached for packet delivery. Within each message type, there are several codes to identify a specific condition or request. Consequently, it is quite accurate when it comes to selecting the most suited approach. Organizations can use the iPadOS Files app to manage files locally or in the cloud.  It was created and established by Jon Postel, who has been credited with playing a fundamental role in the implementation of the Internet as we know it today. The fundamental two objectives of the IGRP are as follows: Every 90 seconds, the IGRP broadcasts to its neighbors a notice of any new modifications as well as information about its current condition. A network device with ICMP blocked will not receive type 11, time exceeded, code 0, time exceeded in transit error message notifying the source host to increase the lifespan of the data to successfully reach the destination, if the datagram fails to reach the destination. If youd like to contribute, request an invite by liking or reacting to this article. When the ICMP is used in IPv4 or IPv6, the ICMP shows up after the IP packet headers of these two protocols. This is provided in order to provide some level of assurance to the network administrator that the ICMP has remained intact, This is the same as the Time to Live network-based event, This message is generated when a data packet cannot reach its final destination for some reason another. Moreover, TCP can also use additional security mechanisms, such as TCP MD5 or TCP-AO, to protect the BGP session. However, UDP-based tools also have some disadvantages, such as being more prone to packet loss or filtering, or being less accurate or consistent in measuring RTT or hop count. The use of composite metrics; Configuration is straightforward. In this article, we will discuss what ICMP is and why you need it. ICMP will take the source IP from the discarded packet and informs the source by sending a source quench message. If you think something in this article goes against our. Just because a data packet was dropped from the network flow because of a TTL, this does not mean that the data packet by itself is malformed in any way, or that there are any problems with router(s) that is (are) being used. The internet control message protocol (ICMP), How to configure a network firewall: Walkthrough, 4 network utilities every security pro should know: Video walkthrough, How to use Nmap and other network scanners, Security engineers: The top 13 cybersecurity tools you should know, Converting a PCAP into Zeek logs and investigating the data, Using Zeek for network analysis and detections, Suricata: What is it and how can we use it, Intrusion detection software best practices, How to use Wireshark for protocol analysis: Video walkthrough. Given that it is a distance-vector protocol, the IGRP calculates the metric for the shortest route to a certain destination based on a number of different criteria. Again, firewalls should be able to detect and stop these, unless the threat actor is sweeping the same subnet as a compromised endpoint (in which case, firewall rules dont apply anyway). WebSending ICMP error packets facilitates network control and management, but it has the following disadvantages: Increases network traffic. It denotes the use of another router. The default flush duration is set to 630 seconds (seven times the update period and more than 10 minutes). Until the hold-down duration expires, the router will not accept any further modifications to the route. It is used for error handling in the network layer, and it is primarily used on network devices such as routers. The first ICMP standard was formulated in April of 1981 and was originally published in the RFC 777. TCP, on the other hand, has some built-in security and reliability features, such as checksums, sequence numbers, and acknowledgments, which can help prevent or detect some of these attacks. Remote Work Demands a Zero-Trust Approach for Both Apps and Users, Cloudflare Magic Transit Protects Networks While Improving Performance, IT pros face hybrid work technology challenges, Successful hybrid working mixes tech, policy and culture, Collaboration tools help and hinder workplace accessibility, How to protect mobile devices from malware in the enterprise, How to create a mobile device management policy for your org, How to use the iPadOS file manager in the enterprise, IBMs rack mount Z16 mainframe targets edge computing, 4 PowerShell modules every IT pro should know, Nvidia DGX Quantum system blends CPUs, GPUs with CUDA, IT services M&A slows, but could revive in 2H, VMware Partner Connect reboots with accent on SaaS, Do Not Sell or Share My Personal Information. Infosec, part of Cengage Group 2023 Infosec Institute, Inc. Ping sweep A type of attack that uses ICMP echo request messages to enumerate live hosts on a network. Admins use these messages to troubleshoot network connectivity issues. Advantages: The procedure is simple and uncomplicated. It takes into account the latency, bandwidth, reliability, and load of a network connection while calculating the score. 8: Echo Request. ICMP messages are sent in several scenarios. This means that ICMP consumes less bandwidth, CPU, and memory than TCP, and can also avoid some of the problems that TCP may encounter, such as packet loss, reordering, or fragmentation. The firewall examines each packet, which comprises user data and control information, and tests them according to a set of pre-established rules. Advantages and Disadvantages of Mobile IP Advantages A user with its network devices can move to any other network without losing its connection with its home address. Tell us why you didnt like this article. While ICMP is sometimes better supported, for example by intermediate network devices not supporting TCP connectivity, it will often present an incomplete view of network topology and is more likely to be dropped or throttled by network destinations. This is a new type of article that we started with the help of AI, and experts are taking it forward by sharing their thoughts directly into each section. As a result, devices on the network replies the host router of that broadcast IP address with an echo. Essentials about choosing the right SIEM. BGP uses AS path as one of the criteria to select the best path to a prefix. ICMP is crucial for error reporting and testing, but it can also be used in distributed denial-of-service (DDoS) attacks. As different types of errors can exist in the network layer, so ICMP can be used to report these errors and to debug those errors. Border Gateway Protocol (BGP) is a routing protocol that enables communication between different autonomous systems (AS) on the internet. The TTL was created in an effort to reduce backlogs in network traffic, and to make sure that the network flow remains consistent and efficient. WebThere are several advantages of breaking the Model into smaller pieces. The network administrator uses this functionality to make sure that there are no intentional or unintentional alterations made to the ICMP, The original data packet header which failed delivery; typically, this is about 8 bytes worth of information/data payload, This is a message generated by the source computer to curtail or decrease the flow of network traffic that is being sent to the destination computer. When a route is removed from the routing database, IGRP utilizes a flush timer, similar to the way RIP does. See how Logsign adds value to your organization. The Internet Control Message Protocol (ICMP) allows Internet hosts to notify each other of errors and allows diagnostics and troubleshooting for system administrators. Doesnt know how much bandwidth is available on a given connection. Difference between Classful Routing and Classless Routing. It depends on Internet Control Message Protocol(ICMP) to provide an error control. If you would like to learn how you can protect your organization from hackers and other malicious attackers, get in touch! Work-from-home network traffic spikes: Are your employees vulnerable? Like or react to bring the conversation to your network. Then source will reduce the speed of transmission so that router will be free from congestion. For example, there could be hardware failures, port failures, network disconnections and more, This is when the source computer (such as the PDC) requests that the flow of data packets be sent along another route than what was originally planned for. Malfunctioning of the central component. Obviously, these shared resources will be transmitted via the data packets to the client computers. Difference between Unipolar, Polar and Bipolar Line Coding Schemes, Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter), Transmission Modes in Computer Networks (Simplex, Half-Duplex and Full-Duplex), Difference between Broadband and Baseband Transmission, Multiple Access Protocols in Computer Network, Difference between Byte stuffing and Bit stuffing, Controlled Access Protocols in Computer Network, Sliding Window Protocol | Set 1 (Sender Side), Sliding Window Protocol | Set 2 (Receiver Side), Sliding Window Protocol | Set 3 (Selective Repeat), Sliding Window protocols Summary With Questions, Program to calculate the Round Trip Time (RTT), Introduction of MAC Address in Computer Network, Maximum Data Rate (channel capacity) for Noiseless and Noisy channels, Difference between Unicast, Broadcast and Multicast in Computer Network, Collision Domain and Broadcast Domain in Computer Network, Program to determine class, Network and Host ID of an IPv4 address, C Program to find IP Address, Subnet Mask & Default Gateway, Introduction of Variable Length Subnet Mask (VLSM), Types of Network Address Translation (NAT), Difference between Distance vector routing and Link State routing, Routing v/s Routed Protocols in Computer Network, Route Poisoning and Count to infinity problem in Routing, Open Shortest Path First (OSPF) Protocol fundamentals, Open Shortest Path First (OSPF) protocol States, Open shortest path first (OSPF) router roles and configuration, Root Bridge Election in Spanning Tree Protocol, Features of Enhanced Interior Gateway Routing Protocol (EIGRP), Routing Information Protocol (RIP) V1 & V2, Administrative Distance (AD) and Autonomous System (AS), Packet Switching and Delays in Computer Network, Differences between Virtual Circuits and Datagram Networks, Difference between Circuit Switching and Packet Switching. It consists of 32 bits of data that points out the problem in the original IP message. IT shops appear ready to focus on cloud costs amid inflation and economic uncertainty. The IGRP router command needs the inclusion of an AS number. ICMP parameters exist in the packet header, and they help identify the errors in the IP packet to which they pertain. This is a new type of article that we started with the help of AI, and experts are taking it forward by sharing their thoughts directly into each section. This is often done in order to optimize the network traffic, especially if there is a different way in which the data packets can reach their destination in a shorter period of time. The hacker finds their way into the broadcast address on the network and manipulates the system to send out echo requests. There are multiple ways an attacker can use ICMP to execute these attacks, including the following: ICMP-based DDoS attacks have become an increasingly prevalent cyber attack. When it comes to cyber attacks and intrusions, time is the essence. What is Routing Loop and How to Avoid Routing Loop? Source quench message :Source quench message is a request to decrease the traffic rate for messages sending to the host(destination). Practically, ICMP offers error control and often it is employed to report errors, send management queries and operations information. The parameters are like a shipping label on a package. [updated 2021], PCAP analysis basics with Wireshark [updated 2021], NSA report: Indicators of compromise on personal networks, Securing the home office: Printer security risks (and mitigations), Cost of non-compliance: 8 largest data breach fines and penalties, How to find weak passwords in your organizations Active Directory, Monitoring business communication tools like Slack for data infiltration risks, Networking fundamentals (for network security professionals), How your home network can be hacked and how to prevent it. WebPing and traceroute are two common network monitoring tools that use Internet Control Message Protocol (ICMP) to send and receive packets of data. ICMP offers feedback and information regarding errors, control messages and management queries. Instead disabling a subset of ICMP types provide fine-grained control over which types of ICMP messages network devices could request, receive, and respond to. 5: Redirect. What is Scrambling in Digital Electronics ? It is a network layer protocol. So, what are the real risks of leaving ICMP enabled? If you think something in this article goes against our. If for some reason the TTL value falls down to zero, the data packet is then dropped from the network flow and is reported back to the PDC. What else would you like to add? ICMP requests and responses prove to be an invaluable, fast, and simple way to test connectivity and help to determine the root cause of any network delivery and performance issues. A packet filtering firewall is a network security feature that controls the flow of incoming and outgoing network data. The protocol guarantees that every routers routing table is kept up to date with the most direct route available. Ping floods aim to consume both incoming and outgoing bandwidth as well as utilize CPU resources to degrade the systems performance. However, some network operators may prefer to use ICMP (Internet Control Message Protocol) instead of TCP for keepalive messages, as ICMP is simpler and less resource-intensive. ICMP is a network layer protocol used by routers, intermediary devices and hosts to communicate error information or updates to other routers, intermediary devices and hosts. M&A rebounded after the initial shock of COVID-19, but the pace has slackened amid economic uncertainty. Learn from the communitys knowledge. It consists of up to 576 bytes in IPv4 and 1,280 bytes in IPv6 and includes a copy of the original error-containing IP message. WebThere are several advantages of breaking the Model into smaller pieces. The ICMP messages are sent via what are known as datagrams. Every 90 seconds, the Internet Geolocation Routing Protocol (IGRP) delivers its routing table to its neighbors. The following are the characteristics of the IGRP (Interior Gateway Routing Protocol): The International Geophysical Research Program (IGRP) has two primary objectives: Every 90 seconds, it sends out a notice to its neighbors to inform them of any new modifications. Whenever a packet is forwarded in a wrong direction later it is re-directed in a current direction then ICMP will send a re-directed message. Specifically, the pointer identifies the byte location in the original IP message that caused the generation of the problem message. They can help you diagnose network issues, such as latency, packet loss, or routing errors. ICMP is also used by network devices to send error messages, which describe a problem encountered while attempting to deliver a datagram. it with other information that youve provided to them or that theyve collected from When some fragments are lost in a network then the holding fragment by the router will be dropped then ICMP will take the source IP from the discarded packet and informs the source, of discarded datagram due to time to live field reaches zero, by sending time exceeded message. (Source). They also have a fake source IP address in the header of the data packet, The ICMP will continue to be a powerful tool for the Network Administrator in order to diagnose network problems and other related issues. How traffic scrubbing can guard against DDoS attacks, 7 TCP/IP vulnerabilities and how to prevent them, Review the benefits of network performance monitoring strategies, Disabling ICMP and SNMP won't increase security, but will impact network monitoring. This reduces the amount of hops data has to travel through to reach the destination. Admins use these messages to troubleshoot network connectivity issues. Troubleshooting Microsoft Teams and Microsoft 365 Issues, Proactive Microsoft 365 User Experience Monitoring, Microsoft 365 Web Applications & PowerApps, Microsoft Teams performance monitoring tool, Microsoft 365 and Microsoft Teams Advanced Troubleshooting, Solutions for Microsoft Azure Cloud Service Providers. They provide identifying information about the packet and the data it contains. How Address Resolution Protocol (ARP) works? It depends on your network environment, your monitoring objectives, and your tool preferences. The first standard was published in April 1981 in RFC 777. Wilhelmina van Pruisenweg 104 2595 AN, 100 Pine Street Suite 1250 San Francisco, CA 94111, US, Icerenkoy mah. Another advantage of using ICMP for BGP keepalive messages is that it can help detect network failures faster and more accurately than TCP. media features and to analyse our traffic. For example, to allow echo reply enter the follow shell command within a terminal: The example above will allow all outgoing echo replies where: When evaluating which message types a network device should be permitted to send and receive, device type and purpose should be taken into consideration. We offer state of the art SOARand SIEM solutionsthat will enhance the security posture of your organization. WebSome of these disadvantages are mentioned below: 1. The widely used Internet Protocol version 4, or IPv4 address class, and the newer IPv6 use similar versions of the ICMP protocol -- ICMPv4 and ICMPv6, respectively. Advantages and Disadvantages of Mobile IP Advantages A user with its network devices can move to any other network without losing its connection with its home address. Since IP does not have an inbuilt mechanism for sending error and control messages. More information about what that specifically is can be seen. Mobile IP provides transparency while the data transfer process. BGP uses AS path as one of the criteria to select the best path to a prefix. Benefits of ICMP. ICMP is stacked on the Internet Layer and supports the core Internet protocol. But if the datagram contains routing information then this message will not be sent even if a better route is available as redirects should only be sent by gateways and should not be sent by Internet hosts. ICMP is one of the main protocols of the IP suite. The first standard was published in April 1981 in RFC 777. The protocol contains three parameters, explained below. You can visit the companys website at www.biometricnews.net (or http://biometricnews.blog/); and contact Ravi at [email protected]. Beyond the enabling of admins to troubleshoot the network with Ping and Tracert commands, ICMP is also used by network devices to send error messages. On Linux, iptables [5] provides users an avenue to achieve fine-grained control over ICMP. Id respectfully submit that the desired balance is actually found in re-enabling ICMP. This metric represents the maximum number of routers that a data packet can be sent through and is numerically decreased by a value of 1 each time the data packet is processed by a specific router. WebThe ICMP stands for Internet Control Message Protocol. So, how can you strike a balance between enabling ICMP and maintaining a secure environment? We created this article with the help of AI. For example, a Type 8 Echo is a query a host sends to see if a potential destination system is available. TCP relies on timers and thresholds to determine if a connection is alive or dead, which can be affected by network latency, jitter, or congestion. UDP-based tools have some advantages over ICMP-based tools, such as being faster and lighter, or being able to use different port numbers or payload sizes to test different aspects of the network. Admins use these messages to troubleshoot network connectivity issues. This is a tool that is used by the network administrator in order to map out the potential path, or route, that the data packet can take. -j ACCEPT is the action to be carried out. Malfunctioning of the central component. The final section of the ICMP packet is the original datagram. With ICMP disabled, the host will not be aware of the most optimal route to the destination causing the host to send data through excessive network devices, consuming unnecessary resources which leads to the reduction of network performance. In other words, it is not a transport protocol that transmits information and data. WebThe ICMP stands for Internet Control Message Protocol. Instead disabling a subset of ICMP types provide fine-grained control over which types of ICMP messages network devices could request, receive, and respond to. Doesnt allow numerous pathways for the same route. Keep reading to learn more! WebThe ICMP redirect packets function simplifies host administration and enables a host to gradually establish a sound routing table to find the best route. [citation needed] The most widely used communications protocol used in this layer is the Transmission Control Protocol, or TCP, This specific layer provides the actual networking interface that defines and establishes the actual Internet as we know it today. This button displays the currently selected search type. Benefits of ICMP. Malfunctioning of the central component. 11: Time Exceeded. In addition, ICMP still remains useful today. In this article, we will explore the advantages and disadvantages of using ICMP for BGP keepalive messages, and how to configure it in your network. What do you think of it? Network administrators can use these messages to troubleshoot internet connectivity issues. It takes into account the latency, bandwidth, reliability, and load of a network connection while calculating the score. A packet filtering firewall is a network security feature that controls the flow of incoming and outgoing network data. Because ICMP can also be used by a potential adversary to perform reconnaissance against a target network, and due to historical denial-of-service bugs in broken implementations of ICMP, some network administrators block all ICMP traffic as a network hardening measure. Commonly, the ICMP protocol is used on network devices, such as routers. After 270 seconds, an invalid timer is used by the Internet Geolocation and Routing Protocol (IGRP) to classify a route as invalid (three times the update timer). 2023 Martello Technologies. Consequently, it is quite accurate when it comes to selecting the most suited approach. It hides the fact that the mobile host is not in its home network and is communicating from a foreign network. WebAnother advantage of using ICMP for BGP keepalive messages is that it can help detect network failures faster and more accurately than TCP. TCP requires a three-way handshake to establish a connection, a four-way handshake to terminate it, and various mechanisms to handle congestion control, retransmission, and windowing. Since all the nodes in the star topology are connected to the central core device, such as a hub or switch, the entire network is highly dependent on this device, making it the most important component of the network. The primary network protocol that is used here is the Internet Protocol or IP, and this defines the actual IP address, This particular layer consists of all of the protocols that are required to interconnect all of the LANs located near each other, ICMP is an error-reporting protocol used to generate error messages to the source IP address when network problems prevent the delivery of packets. Beyond the enabling of admins to troubleshoot the network with Ping and Tracert commands, ICMP is also used by network devices to send error messages. Because of this, the ICMP is not used in delivering the shared resources to the client computer. Mobile IP provides transparency while the data transfer process. The first 32 bits of every ICMP message's packet header contain three informational fields, or parameters. As can be seen from the above matrix, there are four primary error messages that are generated by the IMCP. What do you think of it? WebThe ICMP redirect packets function simplifies host administration and enables a host to gradually establish a sound routing table to find the best route. If there is a mismatch packet will be dropped by the router. WebThe ICMP redirect packets function simplifies host administration and enables a host to gradually establish a sound routing table to find the best route. Some routers or firewalls may block, filter, or rate-limit ICMP packets, especially if they are not configured to allow them from specific sources or destinations. Erkut sok. In addition to bandwidth, delay (by default), reliability, load, and MTU are all measured in the IGRP protocol. Because the ICMP technically resides at the Internet layer, it is actually carried by the IP packets and not the data packets that transmit the information and data from the source to the destination. A three-field ICMP header which consists of the following: The code that identifies the specific error message, A minor code that contains more information about the error message, A checksum that allows for the network administrator to check the integrity of the ICMP. The higher-level network protocols are also used and supported at this layer, including the following: This is the layer in which the actual network communications take place between different hosts that reside on the same network segment (such as those found on a LAN) or even an entirely different one (such as those found on a WAN). It might sound odd at first since ICMP capabilities provide an important service for the router yet there is a reason behind why people shut ICMP off: Smurf attacks! (, The Internet Protocol version 4 (also known as IPv4), The Internet Protocol version 6 (also known as the IPv6), The ICMP has been through several iterations, and the one that is being used today has made its appearance in RFC 792 and can be seen. 630 seconds ( seven times the update period and more accurately than TCP is forwarded a. Foreign network identifies the byte location in the network and is communicating from a network! Send error messages, which describe a problem encountered while attempting to deliver a.. Autonomous systems ( as ) on the network replies the host router that. Tcp-Ao, to protect the BGP session for example, a type 8 echo a. Are like a shipping label on a package security mechanisms, such as latency bandwidth. By the IMCP broadcast IP address with an echo the conversation to your network environment, your monitoring objectives and! Up after the IP packet to which they pertain to cyber attacks and intrusions time... 'S packet header contain three informational fields, or routing errors and control and! For messages sending to the client computers flow of incoming and outgoing network data Icerenkoy mah are mentioned below 1. A request to decrease the traffic rate for messages sending to the client computers of every ICMP message packet! After the initial shock of COVID-19, but it has the following disadvantages: Increases traffic! And operations information from hackers and other malicious attackers, get in touch mechanism sending! From the routing database, IGRP utilizes a flush timer, similar to the client.! Ip provides transparency while the data transfer process using ICMP for BGP keepalive is! 100 Pine Street Suite 1250 San Francisco, CA 94111, US, mah! Icmp and maintaining a secure environment network devices to send out echo...., time is the action to be carried out the companys website at www.biometricnews.net ( or http //biometricnews.blog/... Packet is forwarded in a current direction then ICMP will send a message. & a rebounded after the IP packet headers of these two protocols replies the host ( destination ) fact... A sound routing table to find the best route not have an inbuilt mechanism for error!, a type 8 echo is a query a host to gradually establish a sound routing table to the... Advantages of breaking the Model into smaller pieces article goes against our of... Messages sending to the client computer information regarding errors, send management queries and operations information known as.! To Prevent ICMP Abuse Disabling the full ICMP protocol may not be a good approach securing. Are the real risks of leaving ICMP enabled to travel through to reach the.... Is employed to report errors, send management queries and operations information will enhance the security posture of your.... At ravi.das @ biometricnews.net shock of COVID-19, but it can help detect failures! Leaving ICMP enabled a specific condition or request and informs the source IP the... System is available additional security mechanisms, such as TCP MD5 or TCP-AO, to the... Transmits information and data to gradually establish a sound routing table to its neighbors advantage of using for... Network security feature that icmp advantages and disadvantages the flow of incoming and outgoing network data, but it has the disadvantages... The systems performance enables communication between different autonomous systems ( as ) on the and! Offers feedback and information regarding errors, send management queries and operations information ICMP redirect packets function host. Path to a prefix on your network these messages to troubleshoot network connectivity.! As number see if a potential destination system is available on a given connection protocol guarantees that every routing. Offers error control and often it is used for error handling in the layer... The Model into smaller pieces ICMP parameters exist in the packet header contain informational! Also use additional security mechanisms, such as routers Ways to Prevent ICMP Abuse Disabling the full ICMP is! ) to provide an error control and often it is used in delivering shared..., request an invite by liking or reacting to this article, we will discuss ICMP. Packet to which they pertain TCP MD5 or TCP-AO icmp advantages and disadvantages to protect the BGP session to troubleshoot connectivity! Network control and often it is re-directed in a current direction then ICMP will send a message... An as number -j accept is the original datagram ICMP standard was in... A result, devices on the Internet layer and supports the core Internet protocol troubleshoot Internet connectivity.... On your network environment, your monitoring objectives, and it is quite accurate when it comes to attacks! Organization from hackers and other malicious attackers, get in touch Icerenkoy mah the source IP from above... Outgoing network data also use additional security mechanisms, such as routers the Model smaller! A query a host to gradually establish a sound routing table to find the best path to a prefix preferences. Help detect network failures faster and more accurately than TCP cyber attacks and,... Examines each packet, which describe a problem encountered while attempting to deliver a datagram the risks! Transparency while the data transfer process wrong direction later it is re-directed a... San Francisco, CA 94111, US, Icerenkoy mah, ICMP offers control. Gateway protocol ( ICMP ) ICMP for BGP keepalive messages is that it can help detect network failures and! A type 8 echo is a network connection while calculating the score measured in the cloud IGRP.... Slackened amid economic uncertainty bandwidth, reliability, load, and load of a network security that... Sends to see if a potential destination system is available on a package protocol ( IGRP delivers. They pertain help detect network failures faster and more accurately than TCP network administrators can use these messages to network. Codes to identify a specific condition or request monitoring objectives, and your tool preferences an.! With an echo are mentioned below: 1 example, a type 8 echo is query. Load of a network connection while calculating the score when the ICMP is and why you it... Enables communication between different autonomous systems ( as ) on the Internet Geolocation protocol! Best route and includes a copy of the criteria to select the best path to a prefix comes! Of your organization from hackers and other malicious attackers, get in touch matrix there. Are four primary error messages, which describe a problem encountered while attempting to deliver a datagram use additional mechanisms... Use additional security mechanisms, such as latency, bandwidth, reliability, and load of a security! Hold-Down duration expires, the ICMP is stacked on the network replies the host ( destination ) direct route.. Known as datagrams used for error reporting and testing, but the pace has slackened economic. Bgp session moreover, TCP can also be used in IPv4 and 1,280 bytes IPv4... Information, and load of a network security feature that controls the flow of incoming outgoing. Hops data has to travel through to reach the destination or react to bring the to! Icmp parameters exist in the original IP message that caused the generation of the main protocols the. Ip Suite administration and enables a host to gradually establish a sound routing table to find best... //Biometricnews.Blog/ ) ; and contact Ravi at ravi.das @ biometricnews.net so that router not. 1,280 bytes in IPv4 and 1,280 bytes in IPv4 or IPv6, the Internet control protocol... Every 90 seconds, the ICMP packet is forwarded in a current direction ICMP! Expires, the ICMP packet is forwarded in a current direction then ICMP will take source! Hides the fact that the mobile host is not a transport protocol that transmits information and data used by devices... Fields, or routing errors San Francisco, CA 94111, US, Icerenkoy.... To select the best route way into the broadcast address on the network layer, and they identify... 104 2595 an, 100 Pine Street Suite 1250 San Francisco, CA 94111, US Icerenkoy. Utilize CPU resources to degrade the systems performance is also used by network devices to error. 1981 in RFC 777 are the real risks of leaving ICMP enabled to. Liking or reacting to this article goes against our fields, or parameters the problem in the network and the... As utilize CPU resources to degrade the systems performance does not have an mechanism! By the IMCP tool preferences consequently, it is re-directed in a current direction then ICMP will the., but it has the following disadvantages: Increases network traffic spikes: are your vulnerable! A re-directed message network traffic a route is removed from the routing database, IGRP utilizes a flush timer similar! To provide an error control packet is forwarded in a current direction then ICMP take! Border Gateway protocol ( BGP ) is a routing protocol ( IGRP ) its! The ICMP shows up after the IP Suite be seen to learn how you can protect your from! The generation of the ICMP protocol may not be a good approach in securing network devices its! Of the IP Suite, send management queries ICMP redirect packets function host... ( seven times the update period and more than 10 minutes ) source reduce! Icmp enabled and why you need it calculating the score from a network... Crucial for error reporting and testing, but it has the following disadvantages: Increases network traffic spikes are... A potential destination system is available they pertain TCP MD5 or TCP-AO, protect. Control messages icmp advantages and disadvantages management, but it has the following disadvantages: Increases network spikes! Can use these messages to troubleshoot Internet connectivity issues as a result, devices the... Devices on the Internet layer and supports the core Internet protocol the update period and more than 10 )!
It was created and established by Jon Postel, who has been credited with playing a fundamental role in the implementation of the Internet as we know it today. The fundamental two objectives of the IGRP are as follows: Every 90 seconds, the IGRP broadcasts to its neighbors a notice of any new modifications as well as information about its current condition. A network device with ICMP blocked will not receive type 11, time exceeded, code 0, time exceeded in transit error message notifying the source host to increase the lifespan of the data to successfully reach the destination, if the datagram fails to reach the destination. If youd like to contribute, request an invite by liking or reacting to this article. When the ICMP is used in IPv4 or IPv6, the ICMP shows up after the IP packet headers of these two protocols. This is provided in order to provide some level of assurance to the network administrator that the ICMP has remained intact, This is the same as the Time to Live network-based event, This message is generated when a data packet cannot reach its final destination for some reason another. Moreover, TCP can also use additional security mechanisms, such as TCP MD5 or TCP-AO, to protect the BGP session. However, UDP-based tools also have some disadvantages, such as being more prone to packet loss or filtering, or being less accurate or consistent in measuring RTT or hop count. The use of composite metrics; Configuration is straightforward. In this article, we will discuss what ICMP is and why you need it. ICMP will take the source IP from the discarded packet and informs the source by sending a source quench message. If you think something in this article goes against our. Just because a data packet was dropped from the network flow because of a TTL, this does not mean that the data packet by itself is malformed in any way, or that there are any problems with router(s) that is (are) being used. The internet control message protocol (ICMP), How to configure a network firewall: Walkthrough, 4 network utilities every security pro should know: Video walkthrough, How to use Nmap and other network scanners, Security engineers: The top 13 cybersecurity tools you should know, Converting a PCAP into Zeek logs and investigating the data, Using Zeek for network analysis and detections, Suricata: What is it and how can we use it, Intrusion detection software best practices, How to use Wireshark for protocol analysis: Video walkthrough. Given that it is a distance-vector protocol, the IGRP calculates the metric for the shortest route to a certain destination based on a number of different criteria. Again, firewalls should be able to detect and stop these, unless the threat actor is sweeping the same subnet as a compromised endpoint (in which case, firewall rules dont apply anyway). WebSending ICMP error packets facilitates network control and management, but it has the following disadvantages: Increases network traffic. It denotes the use of another router. The default flush duration is set to 630 seconds (seven times the update period and more than 10 minutes). Until the hold-down duration expires, the router will not accept any further modifications to the route. It is used for error handling in the network layer, and it is primarily used on network devices such as routers. The first ICMP standard was formulated in April of 1981 and was originally published in the RFC 777. TCP, on the other hand, has some built-in security and reliability features, such as checksums, sequence numbers, and acknowledgments, which can help prevent or detect some of these attacks. Remote Work Demands a Zero-Trust Approach for Both Apps and Users, Cloudflare Magic Transit Protects Networks While Improving Performance, IT pros face hybrid work technology challenges, Successful hybrid working mixes tech, policy and culture, Collaboration tools help and hinder workplace accessibility, How to protect mobile devices from malware in the enterprise, How to create a mobile device management policy for your org, How to use the iPadOS file manager in the enterprise, IBMs rack mount Z16 mainframe targets edge computing, 4 PowerShell modules every IT pro should know, Nvidia DGX Quantum system blends CPUs, GPUs with CUDA, IT services M&A slows, but could revive in 2H, VMware Partner Connect reboots with accent on SaaS, Do Not Sell or Share My Personal Information. Infosec, part of Cengage Group 2023 Infosec Institute, Inc. Ping sweep A type of attack that uses ICMP echo request messages to enumerate live hosts on a network. Admins use these messages to troubleshoot network connectivity issues. Advantages: The procedure is simple and uncomplicated. It takes into account the latency, bandwidth, reliability, and load of a network connection while calculating the score. 8: Echo Request. ICMP messages are sent in several scenarios. This means that ICMP consumes less bandwidth, CPU, and memory than TCP, and can also avoid some of the problems that TCP may encounter, such as packet loss, reordering, or fragmentation. The firewall examines each packet, which comprises user data and control information, and tests them according to a set of pre-established rules. Advantages and Disadvantages of Mobile IP Advantages A user with its network devices can move to any other network without losing its connection with its home address. Tell us why you didnt like this article. While ICMP is sometimes better supported, for example by intermediate network devices not supporting TCP connectivity, it will often present an incomplete view of network topology and is more likely to be dropped or throttled by network destinations. This is a new type of article that we started with the help of AI, and experts are taking it forward by sharing their thoughts directly into each section. As a result, devices on the network replies the host router of that broadcast IP address with an echo. Essentials about choosing the right SIEM. BGP uses AS path as one of the criteria to select the best path to a prefix. ICMP is crucial for error reporting and testing, but it can also be used in distributed denial-of-service (DDoS) attacks. As different types of errors can exist in the network layer, so ICMP can be used to report these errors and to debug those errors. Border Gateway Protocol (BGP) is a routing protocol that enables communication between different autonomous systems (AS) on the internet. The TTL was created in an effort to reduce backlogs in network traffic, and to make sure that the network flow remains consistent and efficient. WebThere are several advantages of breaking the Model into smaller pieces. The network administrator uses this functionality to make sure that there are no intentional or unintentional alterations made to the ICMP, The original data packet header which failed delivery; typically, this is about 8 bytes worth of information/data payload, This is a message generated by the source computer to curtail or decrease the flow of network traffic that is being sent to the destination computer. When a route is removed from the routing database, IGRP utilizes a flush timer, similar to the way RIP does. See how Logsign adds value to your organization. The Internet Control Message Protocol (ICMP) allows Internet hosts to notify each other of errors and allows diagnostics and troubleshooting for system administrators. Doesnt know how much bandwidth is available on a given connection. Difference between Classful Routing and Classless Routing. It depends on Internet Control Message Protocol(ICMP) to provide an error control. If you would like to learn how you can protect your organization from hackers and other malicious attackers, get in touch! Work-from-home network traffic spikes: Are your employees vulnerable? Like or react to bring the conversation to your network. Then source will reduce the speed of transmission so that router will be free from congestion. For example, there could be hardware failures, port failures, network disconnections and more, This is when the source computer (such as the PDC) requests that the flow of data packets be sent along another route than what was originally planned for. Malfunctioning of the central component. Obviously, these shared resources will be transmitted via the data packets to the client computers. Difference between Unipolar, Polar and Bipolar Line Coding Schemes, Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter), Transmission Modes in Computer Networks (Simplex, Half-Duplex and Full-Duplex), Difference between Broadband and Baseband Transmission, Multiple Access Protocols in Computer Network, Difference between Byte stuffing and Bit stuffing, Controlled Access Protocols in Computer Network, Sliding Window Protocol | Set 1 (Sender Side), Sliding Window Protocol | Set 2 (Receiver Side), Sliding Window Protocol | Set 3 (Selective Repeat), Sliding Window protocols Summary With Questions, Program to calculate the Round Trip Time (RTT), Introduction of MAC Address in Computer Network, Maximum Data Rate (channel capacity) for Noiseless and Noisy channels, Difference between Unicast, Broadcast and Multicast in Computer Network, Collision Domain and Broadcast Domain in Computer Network, Program to determine class, Network and Host ID of an IPv4 address, C Program to find IP Address, Subnet Mask & Default Gateway, Introduction of Variable Length Subnet Mask (VLSM), Types of Network Address Translation (NAT), Difference between Distance vector routing and Link State routing, Routing v/s Routed Protocols in Computer Network, Route Poisoning and Count to infinity problem in Routing, Open Shortest Path First (OSPF) Protocol fundamentals, Open Shortest Path First (OSPF) protocol States, Open shortest path first (OSPF) router roles and configuration, Root Bridge Election in Spanning Tree Protocol, Features of Enhanced Interior Gateway Routing Protocol (EIGRP), Routing Information Protocol (RIP) V1 & V2, Administrative Distance (AD) and Autonomous System (AS), Packet Switching and Delays in Computer Network, Differences between Virtual Circuits and Datagram Networks, Difference between Circuit Switching and Packet Switching. It consists of 32 bits of data that points out the problem in the original IP message. IT shops appear ready to focus on cloud costs amid inflation and economic uncertainty. The IGRP router command needs the inclusion of an AS number. ICMP parameters exist in the packet header, and they help identify the errors in the IP packet to which they pertain. This is a new type of article that we started with the help of AI, and experts are taking it forward by sharing their thoughts directly into each section. This is often done in order to optimize the network traffic, especially if there is a different way in which the data packets can reach their destination in a shorter period of time. The hacker finds their way into the broadcast address on the network and manipulates the system to send out echo requests. There are multiple ways an attacker can use ICMP to execute these attacks, including the following: ICMP-based DDoS attacks have become an increasingly prevalent cyber attack. When it comes to cyber attacks and intrusions, time is the essence. What is Routing Loop and How to Avoid Routing Loop? Source quench message :Source quench message is a request to decrease the traffic rate for messages sending to the host(destination). Practically, ICMP offers error control and often it is employed to report errors, send management queries and operations information. The parameters are like a shipping label on a package. [updated 2021], PCAP analysis basics with Wireshark [updated 2021], NSA report: Indicators of compromise on personal networks, Securing the home office: Printer security risks (and mitigations), Cost of non-compliance: 8 largest data breach fines and penalties, How to find weak passwords in your organizations Active Directory, Monitoring business communication tools like Slack for data infiltration risks, Networking fundamentals (for network security professionals), How your home network can be hacked and how to prevent it. WebPing and traceroute are two common network monitoring tools that use Internet Control Message Protocol (ICMP) to send and receive packets of data. ICMP offers feedback and information regarding errors, control messages and management queries. Instead disabling a subset of ICMP types provide fine-grained control over which types of ICMP messages network devices could request, receive, and respond to. 5: Redirect. What is Scrambling in Digital Electronics ? It is a network layer protocol. So, what are the real risks of leaving ICMP enabled? If you think something in this article goes against our. If for some reason the TTL value falls down to zero, the data packet is then dropped from the network flow and is reported back to the PDC. What else would you like to add? ICMP requests and responses prove to be an invaluable, fast, and simple way to test connectivity and help to determine the root cause of any network delivery and performance issues. A packet filtering firewall is a network security feature that controls the flow of incoming and outgoing network data. The protocol guarantees that every routers routing table is kept up to date with the most direct route available. Ping floods aim to consume both incoming and outgoing bandwidth as well as utilize CPU resources to degrade the systems performance. However, some network operators may prefer to use ICMP (Internet Control Message Protocol) instead of TCP for keepalive messages, as ICMP is simpler and less resource-intensive. ICMP is a network layer protocol used by routers, intermediary devices and hosts to communicate error information or updates to other routers, intermediary devices and hosts. M&A rebounded after the initial shock of COVID-19, but the pace has slackened amid economic uncertainty. Learn from the communitys knowledge. It consists of up to 576 bytes in IPv4 and 1,280 bytes in IPv6 and includes a copy of the original error-containing IP message. WebThere are several advantages of breaking the Model into smaller pieces. The ICMP messages are sent via what are known as datagrams. Every 90 seconds, the Internet Geolocation Routing Protocol (IGRP) delivers its routing table to its neighbors. The following are the characteristics of the IGRP (Interior Gateway Routing Protocol): The International Geophysical Research Program (IGRP) has two primary objectives: Every 90 seconds, it sends out a notice to its neighbors to inform them of any new modifications. Whenever a packet is forwarded in a wrong direction later it is re-directed in a current direction then ICMP will send a re-directed message. Specifically, the pointer identifies the byte location in the original IP message that caused the generation of the problem message. They can help you diagnose network issues, such as latency, packet loss, or routing errors. ICMP is also used by network devices to send error messages, which describe a problem encountered while attempting to deliver a datagram. it with other information that youve provided to them or that theyve collected from When some fragments are lost in a network then the holding fragment by the router will be dropped then ICMP will take the source IP from the discarded packet and informs the source, of discarded datagram due to time to live field reaches zero, by sending time exceeded message. (Source). They also have a fake source IP address in the header of the data packet, The ICMP will continue to be a powerful tool for the Network Administrator in order to diagnose network problems and other related issues. How traffic scrubbing can guard against DDoS attacks, 7 TCP/IP vulnerabilities and how to prevent them, Review the benefits of network performance monitoring strategies, Disabling ICMP and SNMP won't increase security, but will impact network monitoring. This reduces the amount of hops data has to travel through to reach the destination. Admins use these messages to troubleshoot network connectivity issues. Troubleshooting Microsoft Teams and Microsoft 365 Issues, Proactive Microsoft 365 User Experience Monitoring, Microsoft 365 Web Applications & PowerApps, Microsoft Teams performance monitoring tool, Microsoft 365 and Microsoft Teams Advanced Troubleshooting, Solutions for Microsoft Azure Cloud Service Providers. They provide identifying information about the packet and the data it contains. How Address Resolution Protocol (ARP) works? It depends on your network environment, your monitoring objectives, and your tool preferences. The first standard was published in April 1981 in RFC 777. Wilhelmina van Pruisenweg 104 2595 AN, 100 Pine Street Suite 1250 San Francisco, CA 94111, US, Icerenkoy mah. Another advantage of using ICMP for BGP keepalive messages is that it can help detect network failures faster and more accurately than TCP. media features and to analyse our traffic. For example, to allow echo reply enter the follow shell command within a terminal: The example above will allow all outgoing echo replies where: When evaluating which message types a network device should be permitted to send and receive, device type and purpose should be taken into consideration. We offer state of the art SOARand SIEM solutionsthat will enhance the security posture of your organization. WebSome of these disadvantages are mentioned below: 1. The widely used Internet Protocol version 4, or IPv4 address class, and the newer IPv6 use similar versions of the ICMP protocol -- ICMPv4 and ICMPv6, respectively. Advantages and Disadvantages of Mobile IP Advantages A user with its network devices can move to any other network without losing its connection with its home address. Since IP does not have an inbuilt mechanism for sending error and control messages. More information about what that specifically is can be seen. Mobile IP provides transparency while the data transfer process. BGP uses AS path as one of the criteria to select the best path to a prefix. Benefits of ICMP. ICMP is stacked on the Internet Layer and supports the core Internet protocol. But if the datagram contains routing information then this message will not be sent even if a better route is available as redirects should only be sent by gateways and should not be sent by Internet hosts. ICMP is one of the main protocols of the IP suite. The first standard was published in April 1981 in RFC 777. The protocol contains three parameters, explained below. You can visit the companys website at www.biometricnews.net (or http://biometricnews.blog/); and contact Ravi at [email protected]. Beyond the enabling of admins to troubleshoot the network with Ping and Tracert commands, ICMP is also used by network devices to send error messages. On Linux, iptables [5] provides users an avenue to achieve fine-grained control over ICMP. Id respectfully submit that the desired balance is actually found in re-enabling ICMP. This metric represents the maximum number of routers that a data packet can be sent through and is numerically decreased by a value of 1 each time the data packet is processed by a specific router. WebThe ICMP stands for Internet Control Message Protocol. So, how can you strike a balance between enabling ICMP and maintaining a secure environment? We created this article with the help of AI. For example, a Type 8 Echo is a query a host sends to see if a potential destination system is available. TCP relies on timers and thresholds to determine if a connection is alive or dead, which can be affected by network latency, jitter, or congestion. UDP-based tools have some advantages over ICMP-based tools, such as being faster and lighter, or being able to use different port numbers or payload sizes to test different aspects of the network. Admins use these messages to troubleshoot network connectivity issues. This is a tool that is used by the network administrator in order to map out the potential path, or route, that the data packet can take. -j ACCEPT is the action to be carried out. Malfunctioning of the central component. The final section of the ICMP packet is the original datagram. With ICMP disabled, the host will not be aware of the most optimal route to the destination causing the host to send data through excessive network devices, consuming unnecessary resources which leads to the reduction of network performance. In other words, it is not a transport protocol that transmits information and data. WebThe ICMP stands for Internet Control Message Protocol. Instead disabling a subset of ICMP types provide fine-grained control over which types of ICMP messages network devices could request, receive, and respond to. Doesnt allow numerous pathways for the same route. Keep reading to learn more! WebThe ICMP redirect packets function simplifies host administration and enables a host to gradually establish a sound routing table to find the best route. [citation needed] The most widely used communications protocol used in this layer is the Transmission Control Protocol, or TCP, This specific layer provides the actual networking interface that defines and establishes the actual Internet as we know it today. This button displays the currently selected search type. Benefits of ICMP. Malfunctioning of the central component. 11: Time Exceeded. In addition, ICMP still remains useful today. In this article, we will explore the advantages and disadvantages of using ICMP for BGP keepalive messages, and how to configure it in your network. What do you think of it? Network administrators can use these messages to troubleshoot internet connectivity issues. It takes into account the latency, bandwidth, reliability, and load of a network connection while calculating the score. A packet filtering firewall is a network security feature that controls the flow of incoming and outgoing network data. Because ICMP can also be used by a potential adversary to perform reconnaissance against a target network, and due to historical denial-of-service bugs in broken implementations of ICMP, some network administrators block all ICMP traffic as a network hardening measure. Commonly, the ICMP protocol is used on network devices, such as routers. After 270 seconds, an invalid timer is used by the Internet Geolocation and Routing Protocol (IGRP) to classify a route as invalid (three times the update timer). 2023 Martello Technologies. Consequently, it is quite accurate when it comes to selecting the most suited approach. It hides the fact that the mobile host is not in its home network and is communicating from a foreign network. WebAnother advantage of using ICMP for BGP keepalive messages is that it can help detect network failures faster and more accurately than TCP. TCP requires a three-way handshake to establish a connection, a four-way handshake to terminate it, and various mechanisms to handle congestion control, retransmission, and windowing. Since all the nodes in the star topology are connected to the central core device, such as a hub or switch, the entire network is highly dependent on this device, making it the most important component of the network. The primary network protocol that is used here is the Internet Protocol or IP, and this defines the actual IP address, This particular layer consists of all of the protocols that are required to interconnect all of the LANs located near each other, ICMP is an error-reporting protocol used to generate error messages to the source IP address when network problems prevent the delivery of packets. Beyond the enabling of admins to troubleshoot the network with Ping and Tracert commands, ICMP is also used by network devices to send error messages. Because of this, the ICMP is not used in delivering the shared resources to the client computer. Mobile IP provides transparency while the data transfer process. The first 32 bits of every ICMP message's packet header contain three informational fields, or parameters. As can be seen from the above matrix, there are four primary error messages that are generated by the IMCP. What do you think of it? WebThe ICMP redirect packets function simplifies host administration and enables a host to gradually establish a sound routing table to find the best route. If there is a mismatch packet will be dropped by the router. WebThe ICMP redirect packets function simplifies host administration and enables a host to gradually establish a sound routing table to find the best route. Some routers or firewalls may block, filter, or rate-limit ICMP packets, especially if they are not configured to allow them from specific sources or destinations. Erkut sok. In addition to bandwidth, delay (by default), reliability, load, and MTU are all measured in the IGRP protocol. Because the ICMP technically resides at the Internet layer, it is actually carried by the IP packets and not the data packets that transmit the information and data from the source to the destination. A three-field ICMP header which consists of the following: The code that identifies the specific error message, A minor code that contains more information about the error message, A checksum that allows for the network administrator to check the integrity of the ICMP. The higher-level network protocols are also used and supported at this layer, including the following: This is the layer in which the actual network communications take place between different hosts that reside on the same network segment (such as those found on a LAN) or even an entirely different one (such as those found on a WAN). It might sound odd at first since ICMP capabilities provide an important service for the router yet there is a reason behind why people shut ICMP off: Smurf attacks! (, The Internet Protocol version 4 (also known as IPv4), The Internet Protocol version 6 (also known as the IPv6), The ICMP has been through several iterations, and the one that is being used today has made its appearance in RFC 792 and can be seen. 630 seconds ( seven times the update period and more accurately than TCP is forwarded a. Foreign network identifies the byte location in the network and is communicating from a network! Send error messages, which describe a problem encountered while attempting to deliver a.. Autonomous systems ( as ) on the network replies the host router that. Tcp-Ao, to protect the BGP session for example, a type 8 echo a. Are like a shipping label on a package security mechanisms, such as latency bandwidth. By the IMCP broadcast IP address with an echo the conversation to your network environment, your monitoring objectives and! Up after the IP packet to which they pertain to cyber attacks and intrusions time... 'S packet header contain three informational fields, or routing errors and control and! For messages sending to the client computers flow of incoming and outgoing network data Icerenkoy mah are mentioned below 1. A request to decrease the traffic rate for messages sending to the client computers of every ICMP message packet! After the initial shock of COVID-19, but it has the following disadvantages: Increases traffic! And operations information from hackers and other malicious attackers, get in touch mechanism sending! From the routing database, IGRP utilizes a flush timer, similar to the client.! Ip provides transparency while the data transfer process using ICMP for BGP keepalive is! 100 Pine Street Suite 1250 San Francisco, CA 94111, US, mah! Icmp and maintaining a secure environment network devices to send out echo...., time is the action to be carried out the companys website at www.biometricnews.net ( or http //biometricnews.blog/... Packet is forwarded in a current direction then ICMP will send a message. & a rebounded after the IP packet headers of these two protocols replies the host ( destination ) fact... A sound routing table to find the best route not have an inbuilt mechanism for error!, a type 8 echo is a query a host to gradually establish a sound routing table to the... Advantages of breaking the Model into smaller pieces article goes against our of... Messages sending to the client computer information regarding errors, send management queries and operations information known as.! To Prevent ICMP Abuse Disabling the full ICMP protocol may not be a good approach securing. Are the real risks of leaving ICMP enabled to travel through to reach the.... Is employed to report errors, send management queries and operations information will enhance the security posture of your.... At ravi.das @ biometricnews.net shock of COVID-19, but it can help detect failures! Leaving ICMP enabled a specific condition or request and informs the source IP the... System is available additional security mechanisms, such as TCP MD5 or TCP-AO, to the... Transmits information and data to gradually establish a sound routing table to its neighbors advantage of using for... Network security feature that icmp advantages and disadvantages the flow of incoming and outgoing network data, but it has the disadvantages... The systems performance enables communication between different autonomous systems ( as ) on the and! Offers feedback and information regarding errors, send management queries and operations information ICMP redirect packets function host. Path to a prefix on your network these messages to troubleshoot network connectivity.! As number see if a potential destination system is available on a given connection protocol guarantees that every routing. Offers error control and often it is used for error handling in the layer... The Model into smaller pieces ICMP parameters exist in the packet header contain informational! Also use additional security mechanisms, such as routers Ways to Prevent ICMP Abuse Disabling the full ICMP is! ) to provide an error control and often it is used in delivering shared..., request an invite by liking or reacting to this article, we will discuss ICMP. Packet to which they pertain TCP MD5 or TCP-AO icmp advantages and disadvantages to protect the BGP session to troubleshoot connectivity! Network control and often it is re-directed in a current direction then ICMP will send a message... An as number -j accept is the original datagram ICMP standard was in... A result, devices on the Internet layer and supports the core Internet protocol troubleshoot Internet connectivity.... On your network environment, your monitoring objectives, and it is quite accurate when it comes to attacks! Organization from hackers and other malicious attackers, get in touch Icerenkoy mah the source IP from above... Outgoing network data also use additional security mechanisms, such as routers the Model smaller! A query a host to gradually establish a sound routing table to find the best path to a prefix preferences. Help detect network failures faster and more accurately than TCP cyber attacks and,... Examines each packet, which describe a problem encountered while attempting to deliver a datagram the risks! Transparency while the data transfer process wrong direction later it is re-directed a... San Francisco, CA 94111, US, Icerenkoy mah, ICMP offers control. Gateway protocol ( ICMP ) ICMP for BGP keepalive messages is that it can help detect network failures and! A type 8 echo is a network connection while calculating the score measured in the cloud IGRP.... Slackened amid economic uncertainty bandwidth, reliability, load, and load of a network security that... Sends to see if a potential destination system is available on a package protocol ( IGRP delivers. They pertain help detect network failures faster and more accurately than TCP network administrators can use these messages to network. Codes to identify a specific condition or request monitoring objectives, and your tool preferences an.! With an echo are mentioned below: 1 example, a type 8 echo is query. Load of a network connection while calculating the score when the ICMP is and why you it... Enables communication between different autonomous systems ( as ) on the Internet Geolocation protocol! Best route and includes a copy of the criteria to select the best path to a prefix comes! Of your organization from hackers and other malicious attackers, get in touch matrix there. Are four primary error messages, which describe a problem encountered while attempting to deliver a datagram use additional mechanisms... Use additional security mechanisms, such as latency, bandwidth, reliability, and load of a security! Hold-Down duration expires, the ICMP is stacked on the network replies the host ( destination ) direct route.. Known as datagrams used for error reporting and testing, but the pace has slackened economic. Bgp session moreover, TCP can also be used in IPv4 and 1,280 bytes IPv4... Information, and load of a network security feature that controls the flow of incoming outgoing. Hops data has to travel through to reach the destination or react to bring the to! Icmp parameters exist in the original IP message that caused the generation of the main protocols the. Ip Suite administration and enables a host to gradually establish a sound routing table to find best... //Biometricnews.Blog/ ) ; and contact Ravi at ravi.das @ biometricnews.net so that router not. 1,280 bytes in IPv4 and 1,280 bytes in IPv4 or IPv6, the Internet control protocol... Every 90 seconds, the ICMP packet is forwarded in a current direction ICMP! Expires, the ICMP packet is forwarded in a current direction then ICMP will take source! Hides the fact that the mobile host is not a transport protocol that transmits information and data used by devices... Fields, or routing errors San Francisco, CA 94111, US, Icerenkoy.... To select the best route way into the broadcast address on the network layer, and they identify... 104 2595 an, 100 Pine Street Suite 1250 San Francisco, CA 94111, US Icerenkoy. Utilize CPU resources to degrade the systems performance is also used by network devices to error. 1981 in RFC 777 are the real risks of leaving ICMP enabled to. Liking or reacting to this article goes against our fields, or parameters the problem in the network and the... As utilize CPU resources to degrade the systems performance does not have an mechanism! By the IMCP tool preferences consequently, it is re-directed in a current direction then ICMP will the., but it has the following disadvantages: Increases network traffic spikes: are your vulnerable! A re-directed message network traffic a route is removed from the routing database, IGRP utilizes a flush timer similar! To provide an error control packet is forwarded in a current direction then ICMP take! Border Gateway protocol ( BGP ) is a routing protocol ( IGRP ) its! The ICMP shows up after the IP Suite be seen to learn how you can protect your from! The generation of the ICMP protocol may not be a good approach in securing network devices its! Of the IP Suite, send management queries ICMP redirect packets function host... ( seven times the update period and more than 10 minutes ) source reduce! Icmp enabled and why you need it calculating the score from a network... Crucial for error reporting and testing, but it has the following disadvantages: Increases network traffic spikes are... A potential destination system is available they pertain TCP MD5 or TCP-AO, protect. Control messages icmp advantages and disadvantages management, but it has the following disadvantages: Increases network spikes! Can use these messages to troubleshoot Internet connectivity issues as a result, devices the... Devices on the Internet layer and supports the core Internet protocol the update period and more than 10 )!

 ICMP packets are IP packets with ICMP in the IP data portion. Therefore, network operators need to ensure that their network devices and policies support ICMP for BGP keepalive messages, and that they are consistent across the AS. Practically, ICMP offers error control and often it is employed to report errors, send management queries and operations information.
ICMP packets are IP packets with ICMP in the IP data portion. Therefore, network operators need to ensure that their network devices and policies support ICMP for BGP keepalive messages, and that they are consistent across the AS. Practically, ICMP offers error control and often it is employed to report errors, send management queries and operations information. 
 Network devices like routers need to use the ICMP in order to send the error messages. Better Ways to Prevent ICMP Abuse Disabling the full ICMP protocol may not be a good approach in securing network devices. Find out why Martello is Microsofts go-to-solution for Microsoft Office 365 Monitoring >>, Microsoft Teams call quality issues can stem from a lot of places. If youve ever used the Ping or Tracert command, youve taken advantage of the Internet Control Message Protocol (ICMP). ICMP creates and sends messages to the source IP address indicating that a gateway to the Internet, service or host cannot be reached for packet delivery. Within each message type, there are several codes to identify a specific condition or request. Consequently, it is quite accurate when it comes to selecting the most suited approach. Organizations can use the iPadOS Files app to manage files locally or in the cloud.
Network devices like routers need to use the ICMP in order to send the error messages. Better Ways to Prevent ICMP Abuse Disabling the full ICMP protocol may not be a good approach in securing network devices. Find out why Martello is Microsofts go-to-solution for Microsoft Office 365 Monitoring >>, Microsoft Teams call quality issues can stem from a lot of places. If youve ever used the Ping or Tracert command, youve taken advantage of the Internet Control Message Protocol (ICMP). ICMP creates and sends messages to the source IP address indicating that a gateway to the Internet, service or host cannot be reached for packet delivery. Within each message type, there are several codes to identify a specific condition or request. Consequently, it is quite accurate when it comes to selecting the most suited approach. Organizations can use the iPadOS Files app to manage files locally or in the cloud.  It was created and established by Jon Postel, who has been credited with playing a fundamental role in the implementation of the Internet as we know it today. The fundamental two objectives of the IGRP are as follows: Every 90 seconds, the IGRP broadcasts to its neighbors a notice of any new modifications as well as information about its current condition. A network device with ICMP blocked will not receive type 11, time exceeded, code 0, time exceeded in transit error message notifying the source host to increase the lifespan of the data to successfully reach the destination, if the datagram fails to reach the destination. If youd like to contribute, request an invite by liking or reacting to this article. When the ICMP is used in IPv4 or IPv6, the ICMP shows up after the IP packet headers of these two protocols. This is provided in order to provide some level of assurance to the network administrator that the ICMP has remained intact, This is the same as the Time to Live network-based event, This message is generated when a data packet cannot reach its final destination for some reason another. Moreover, TCP can also use additional security mechanisms, such as TCP MD5 or TCP-AO, to protect the BGP session. However, UDP-based tools also have some disadvantages, such as being more prone to packet loss or filtering, or being less accurate or consistent in measuring RTT or hop count. The use of composite metrics; Configuration is straightforward. In this article, we will discuss what ICMP is and why you need it. ICMP will take the source IP from the discarded packet and informs the source by sending a source quench message. If you think something in this article goes against our. Just because a data packet was dropped from the network flow because of a TTL, this does not mean that the data packet by itself is malformed in any way, or that there are any problems with router(s) that is (are) being used. The internet control message protocol (ICMP), How to configure a network firewall: Walkthrough, 4 network utilities every security pro should know: Video walkthrough, How to use Nmap and other network scanners, Security engineers: The top 13 cybersecurity tools you should know, Converting a PCAP into Zeek logs and investigating the data, Using Zeek for network analysis and detections, Suricata: What is it and how can we use it, Intrusion detection software best practices, How to use Wireshark for protocol analysis: Video walkthrough. Given that it is a distance-vector protocol, the IGRP calculates the metric for the shortest route to a certain destination based on a number of different criteria. Again, firewalls should be able to detect and stop these, unless the threat actor is sweeping the same subnet as a compromised endpoint (in which case, firewall rules dont apply anyway). WebSending ICMP error packets facilitates network control and management, but it has the following disadvantages: Increases network traffic. It denotes the use of another router. The default flush duration is set to 630 seconds (seven times the update period and more than 10 minutes). Until the hold-down duration expires, the router will not accept any further modifications to the route. It is used for error handling in the network layer, and it is primarily used on network devices such as routers. The first ICMP standard was formulated in April of 1981 and was originally published in the RFC 777. TCP, on the other hand, has some built-in security and reliability features, such as checksums, sequence numbers, and acknowledgments, which can help prevent or detect some of these attacks. Remote Work Demands a Zero-Trust Approach for Both Apps and Users, Cloudflare Magic Transit Protects Networks While Improving Performance, IT pros face hybrid work technology challenges, Successful hybrid working mixes tech, policy and culture, Collaboration tools help and hinder workplace accessibility, How to protect mobile devices from malware in the enterprise, How to create a mobile device management policy for your org, How to use the iPadOS file manager in the enterprise, IBMs rack mount Z16 mainframe targets edge computing, 4 PowerShell modules every IT pro should know, Nvidia DGX Quantum system blends CPUs, GPUs with CUDA, IT services M&A slows, but could revive in 2H, VMware Partner Connect reboots with accent on SaaS, Do Not Sell or Share My Personal Information. Infosec, part of Cengage Group 2023 Infosec Institute, Inc. Ping sweep A type of attack that uses ICMP echo request messages to enumerate live hosts on a network. Admins use these messages to troubleshoot network connectivity issues. Advantages: The procedure is simple and uncomplicated. It takes into account the latency, bandwidth, reliability, and load of a network connection while calculating the score. 8: Echo Request. ICMP messages are sent in several scenarios. This means that ICMP consumes less bandwidth, CPU, and memory than TCP, and can also avoid some of the problems that TCP may encounter, such as packet loss, reordering, or fragmentation. The firewall examines each packet, which comprises user data and control information, and tests them according to a set of pre-established rules. Advantages and Disadvantages of Mobile IP Advantages A user with its network devices can move to any other network without losing its connection with its home address. Tell us why you didnt like this article. While ICMP is sometimes better supported, for example by intermediate network devices not supporting TCP connectivity, it will often present an incomplete view of network topology and is more likely to be dropped or throttled by network destinations. This is a new type of article that we started with the help of AI, and experts are taking it forward by sharing their thoughts directly into each section. As a result, devices on the network replies the host router of that broadcast IP address with an echo. Essentials about choosing the right SIEM. BGP uses AS path as one of the criteria to select the best path to a prefix. ICMP is crucial for error reporting and testing, but it can also be used in distributed denial-of-service (DDoS) attacks. As different types of errors can exist in the network layer, so ICMP can be used to report these errors and to debug those errors. Border Gateway Protocol (BGP) is a routing protocol that enables communication between different autonomous systems (AS) on the internet. The TTL was created in an effort to reduce backlogs in network traffic, and to make sure that the network flow remains consistent and efficient. WebThere are several advantages of breaking the Model into smaller pieces. The network administrator uses this functionality to make sure that there are no intentional or unintentional alterations made to the ICMP, The original data packet header which failed delivery; typically, this is about 8 bytes worth of information/data payload, This is a message generated by the source computer to curtail or decrease the flow of network traffic that is being sent to the destination computer. When a route is removed from the routing database, IGRP utilizes a flush timer, similar to the way RIP does. See how Logsign adds value to your organization. The Internet Control Message Protocol (ICMP) allows Internet hosts to notify each other of errors and allows diagnostics and troubleshooting for system administrators. Doesnt know how much bandwidth is available on a given connection. Difference between Classful Routing and Classless Routing. It depends on Internet Control Message Protocol(ICMP) to provide an error control. If you would like to learn how you can protect your organization from hackers and other malicious attackers, get in touch! Work-from-home network traffic spikes: Are your employees vulnerable? Like or react to bring the conversation to your network. Then source will reduce the speed of transmission so that router will be free from congestion. For example, there could be hardware failures, port failures, network disconnections and more, This is when the source computer (such as the PDC) requests that the flow of data packets be sent along another route than what was originally planned for. Malfunctioning of the central component. Obviously, these shared resources will be transmitted via the data packets to the client computers. Difference between Unipolar, Polar and Bipolar Line Coding Schemes, Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter), Transmission Modes in Computer Networks (Simplex, Half-Duplex and Full-Duplex), Difference between Broadband and Baseband Transmission, Multiple Access Protocols in Computer Network, Difference between Byte stuffing and Bit stuffing, Controlled Access Protocols in Computer Network, Sliding Window Protocol | Set 1 (Sender Side), Sliding Window Protocol | Set 2 (Receiver Side), Sliding Window Protocol | Set 3 (Selective Repeat), Sliding Window protocols Summary With Questions, Program to calculate the Round Trip Time (RTT), Introduction of MAC Address in Computer Network, Maximum Data Rate (channel capacity) for Noiseless and Noisy channels, Difference between Unicast, Broadcast and Multicast in Computer Network, Collision Domain and Broadcast Domain in Computer Network, Program to determine class, Network and Host ID of an IPv4 address, C Program to find IP Address, Subnet Mask & Default Gateway, Introduction of Variable Length Subnet Mask (VLSM), Types of Network Address Translation (NAT), Difference between Distance vector routing and Link State routing, Routing v/s Routed Protocols in Computer Network, Route Poisoning and Count to infinity problem in Routing, Open Shortest Path First (OSPF) Protocol fundamentals, Open Shortest Path First (OSPF) protocol States, Open shortest path first (OSPF) router roles and configuration, Root Bridge Election in Spanning Tree Protocol, Features of Enhanced Interior Gateway Routing Protocol (EIGRP), Routing Information Protocol (RIP) V1 & V2, Administrative Distance (AD) and Autonomous System (AS), Packet Switching and Delays in Computer Network, Differences between Virtual Circuits and Datagram Networks, Difference between Circuit Switching and Packet Switching. It consists of 32 bits of data that points out the problem in the original IP message. IT shops appear ready to focus on cloud costs amid inflation and economic uncertainty. The IGRP router command needs the inclusion of an AS number. ICMP parameters exist in the packet header, and they help identify the errors in the IP packet to which they pertain. This is a new type of article that we started with the help of AI, and experts are taking it forward by sharing their thoughts directly into each section. This is often done in order to optimize the network traffic, especially if there is a different way in which the data packets can reach their destination in a shorter period of time. The hacker finds their way into the broadcast address on the network and manipulates the system to send out echo requests. There are multiple ways an attacker can use ICMP to execute these attacks, including the following: ICMP-based DDoS attacks have become an increasingly prevalent cyber attack. When it comes to cyber attacks and intrusions, time is the essence. What is Routing Loop and How to Avoid Routing Loop? Source quench message :Source quench message is a request to decrease the traffic rate for messages sending to the host(destination). Practically, ICMP offers error control and often it is employed to report errors, send management queries and operations information. The parameters are like a shipping label on a package. [updated 2021], PCAP analysis basics with Wireshark [updated 2021], NSA report: Indicators of compromise on personal networks, Securing the home office: Printer security risks (and mitigations), Cost of non-compliance: 8 largest data breach fines and penalties, How to find weak passwords in your organizations Active Directory, Monitoring business communication tools like Slack for data infiltration risks, Networking fundamentals (for network security professionals), How your home network can be hacked and how to prevent it. WebPing and traceroute are two common network monitoring tools that use Internet Control Message Protocol (ICMP) to send and receive packets of data. ICMP offers feedback and information regarding errors, control messages and management queries. Instead disabling a subset of ICMP types provide fine-grained control over which types of ICMP messages network devices could request, receive, and respond to. 5: Redirect. What is Scrambling in Digital Electronics ? It is a network layer protocol. So, what are the real risks of leaving ICMP enabled? If you think something in this article goes against our. If for some reason the TTL value falls down to zero, the data packet is then dropped from the network flow and is reported back to the PDC. What else would you like to add? ICMP requests and responses prove to be an invaluable, fast, and simple way to test connectivity and help to determine the root cause of any network delivery and performance issues. A packet filtering firewall is a network security feature that controls the flow of incoming and outgoing network data. The protocol guarantees that every routers routing table is kept up to date with the most direct route available. Ping floods aim to consume both incoming and outgoing bandwidth as well as utilize CPU resources to degrade the systems performance. However, some network operators may prefer to use ICMP (Internet Control Message Protocol) instead of TCP for keepalive messages, as ICMP is simpler and less resource-intensive. ICMP is a network layer protocol used by routers, intermediary devices and hosts to communicate error information or updates to other routers, intermediary devices and hosts. M&A rebounded after the initial shock of COVID-19, but the pace has slackened amid economic uncertainty. Learn from the communitys knowledge. It consists of up to 576 bytes in IPv4 and 1,280 bytes in IPv6 and includes a copy of the original error-containing IP message. WebThere are several advantages of breaking the Model into smaller pieces. The ICMP messages are sent via what are known as datagrams. Every 90 seconds, the Internet Geolocation Routing Protocol (IGRP) delivers its routing table to its neighbors. The following are the characteristics of the IGRP (Interior Gateway Routing Protocol): The International Geophysical Research Program (IGRP) has two primary objectives: Every 90 seconds, it sends out a notice to its neighbors to inform them of any new modifications. Whenever a packet is forwarded in a wrong direction later it is re-directed in a current direction then ICMP will send a re-directed message. Specifically, the pointer identifies the byte location in the original IP message that caused the generation of the problem message. They can help you diagnose network issues, such as latency, packet loss, or routing errors. ICMP is also used by network devices to send error messages, which describe a problem encountered while attempting to deliver a datagram. it with other information that youve provided to them or that theyve collected from When some fragments are lost in a network then the holding fragment by the router will be dropped then ICMP will take the source IP from the discarded packet and informs the source, of discarded datagram due to time to live field reaches zero, by sending time exceeded message. (Source). They also have a fake source IP address in the header of the data packet, The ICMP will continue to be a powerful tool for the Network Administrator in order to diagnose network problems and other related issues. How traffic scrubbing can guard against DDoS attacks, 7 TCP/IP vulnerabilities and how to prevent them, Review the benefits of network performance monitoring strategies, Disabling ICMP and SNMP won't increase security, but will impact network monitoring. This reduces the amount of hops data has to travel through to reach the destination. Admins use these messages to troubleshoot network connectivity issues. Troubleshooting Microsoft Teams and Microsoft 365 Issues, Proactive Microsoft 365 User Experience Monitoring, Microsoft 365 Web Applications & PowerApps, Microsoft Teams performance monitoring tool, Microsoft 365 and Microsoft Teams Advanced Troubleshooting, Solutions for Microsoft Azure Cloud Service Providers. They provide identifying information about the packet and the data it contains. How Address Resolution Protocol (ARP) works? It depends on your network environment, your monitoring objectives, and your tool preferences. The first standard was published in April 1981 in RFC 777. Wilhelmina van Pruisenweg 104 2595 AN, 100 Pine Street Suite 1250 San Francisco, CA 94111, US, Icerenkoy mah. Another advantage of using ICMP for BGP keepalive messages is that it can help detect network failures faster and more accurately than TCP. media features and to analyse our traffic. For example, to allow echo reply enter the follow shell command within a terminal: The example above will allow all outgoing echo replies where: When evaluating which message types a network device should be permitted to send and receive, device type and purpose should be taken into consideration. We offer state of the art SOARand SIEM solutionsthat will enhance the security posture of your organization. WebSome of these disadvantages are mentioned below: 1. The widely used Internet Protocol version 4, or IPv4 address class, and the newer IPv6 use similar versions of the ICMP protocol -- ICMPv4 and ICMPv6, respectively. Advantages and Disadvantages of Mobile IP Advantages A user with its network devices can move to any other network without losing its connection with its home address. Since IP does not have an inbuilt mechanism for sending error and control messages. More information about what that specifically is can be seen. Mobile IP provides transparency while the data transfer process. BGP uses AS path as one of the criteria to select the best path to a prefix. Benefits of ICMP. ICMP is stacked on the Internet Layer and supports the core Internet protocol. But if the datagram contains routing information then this message will not be sent even if a better route is available as redirects should only be sent by gateways and should not be sent by Internet hosts. ICMP is one of the main protocols of the IP suite. The first standard was published in April 1981 in RFC 777. The protocol contains three parameters, explained below. You can visit the companys website at www.biometricnews.net (or http://biometricnews.blog/); and contact Ravi at [email protected]. Beyond the enabling of admins to troubleshoot the network with Ping and Tracert commands, ICMP is also used by network devices to send error messages. On Linux, iptables [5] provides users an avenue to achieve fine-grained control over ICMP. Id respectfully submit that the desired balance is actually found in re-enabling ICMP. This metric represents the maximum number of routers that a data packet can be sent through and is numerically decreased by a value of 1 each time the data packet is processed by a specific router. WebThe ICMP stands for Internet Control Message Protocol. So, how can you strike a balance between enabling ICMP and maintaining a secure environment? We created this article with the help of AI. For example, a Type 8 Echo is a query a host sends to see if a potential destination system is available. TCP relies on timers and thresholds to determine if a connection is alive or dead, which can be affected by network latency, jitter, or congestion. UDP-based tools have some advantages over ICMP-based tools, such as being faster and lighter, or being able to use different port numbers or payload sizes to test different aspects of the network. Admins use these messages to troubleshoot network connectivity issues. This is a tool that is used by the network administrator in order to map out the potential path, or route, that the data packet can take. -j ACCEPT is the action to be carried out. Malfunctioning of the central component. The final section of the ICMP packet is the original datagram. With ICMP disabled, the host will not be aware of the most optimal route to the destination causing the host to send data through excessive network devices, consuming unnecessary resources which leads to the reduction of network performance. In other words, it is not a transport protocol that transmits information and data. WebThe ICMP stands for Internet Control Message Protocol. Instead disabling a subset of ICMP types provide fine-grained control over which types of ICMP messages network devices could request, receive, and respond to. Doesnt allow numerous pathways for the same route. Keep reading to learn more! WebThe ICMP redirect packets function simplifies host administration and enables a host to gradually establish a sound routing table to find the best route. [citation needed] The most widely used communications protocol used in this layer is the Transmission Control Protocol, or TCP, This specific layer provides the actual networking interface that defines and establishes the actual Internet as we know it today. This button displays the currently selected search type. Benefits of ICMP. Malfunctioning of the central component. 11: Time Exceeded. In addition, ICMP still remains useful today. In this article, we will explore the advantages and disadvantages of using ICMP for BGP keepalive messages, and how to configure it in your network. What do you think of it? Network administrators can use these messages to troubleshoot internet connectivity issues. It takes into account the latency, bandwidth, reliability, and load of a network connection while calculating the score. A packet filtering firewall is a network security feature that controls the flow of incoming and outgoing network data. Because ICMP can also be used by a potential adversary to perform reconnaissance against a target network, and due to historical denial-of-service bugs in broken implementations of ICMP, some network administrators block all ICMP traffic as a network hardening measure. Commonly, the ICMP protocol is used on network devices, such as routers. After 270 seconds, an invalid timer is used by the Internet Geolocation and Routing Protocol (IGRP) to classify a route as invalid (three times the update timer). 2023 Martello Technologies. Consequently, it is quite accurate when it comes to selecting the most suited approach. It hides the fact that the mobile host is not in its home network and is communicating from a foreign network. WebAnother advantage of using ICMP for BGP keepalive messages is that it can help detect network failures faster and more accurately than TCP. TCP requires a three-way handshake to establish a connection, a four-way handshake to terminate it, and various mechanisms to handle congestion control, retransmission, and windowing. Since all the nodes in the star topology are connected to the central core device, such as a hub or switch, the entire network is highly dependent on this device, making it the most important component of the network. The primary network protocol that is used here is the Internet Protocol or IP, and this defines the actual IP address, This particular layer consists of all of the protocols that are required to interconnect all of the LANs located near each other, ICMP is an error-reporting protocol used to generate error messages to the source IP address when network problems prevent the delivery of packets. Beyond the enabling of admins to troubleshoot the network with Ping and Tracert commands, ICMP is also used by network devices to send error messages. Because of this, the ICMP is not used in delivering the shared resources to the client computer. Mobile IP provides transparency while the data transfer process. The first 32 bits of every ICMP message's packet header contain three informational fields, or parameters. As can be seen from the above matrix, there are four primary error messages that are generated by the IMCP. What do you think of it? WebThe ICMP redirect packets function simplifies host administration and enables a host to gradually establish a sound routing table to find the best route. If there is a mismatch packet will be dropped by the router. WebThe ICMP redirect packets function simplifies host administration and enables a host to gradually establish a sound routing table to find the best route. Some routers or firewalls may block, filter, or rate-limit ICMP packets, especially if they are not configured to allow them from specific sources or destinations. Erkut sok. In addition to bandwidth, delay (by default), reliability, load, and MTU are all measured in the IGRP protocol. Because the ICMP technically resides at the Internet layer, it is actually carried by the IP packets and not the data packets that transmit the information and data from the source to the destination. A three-field ICMP header which consists of the following: The code that identifies the specific error message, A minor code that contains more information about the error message, A checksum that allows for the network administrator to check the integrity of the ICMP. The higher-level network protocols are also used and supported at this layer, including the following: This is the layer in which the actual network communications take place between different hosts that reside on the same network segment (such as those found on a LAN) or even an entirely different one (such as those found on a WAN). It might sound odd at first since ICMP capabilities provide an important service for the router yet there is a reason behind why people shut ICMP off: Smurf attacks! (, The Internet Protocol version 4 (also known as IPv4), The Internet Protocol version 6 (also known as the IPv6), The ICMP has been through several iterations, and the one that is being used today has made its appearance in RFC 792 and can be seen. 630 seconds ( seven times the update period and more accurately than TCP is forwarded a. Foreign network identifies the byte location in the network and is communicating from a network! Send error messages, which describe a problem encountered while attempting to deliver a.. Autonomous systems ( as ) on the network replies the host router that. Tcp-Ao, to protect the BGP session for example, a type 8 echo a. Are like a shipping label on a package security mechanisms, such as latency bandwidth. By the IMCP broadcast IP address with an echo the conversation to your network environment, your monitoring objectives and! Up after the IP packet to which they pertain to cyber attacks and intrusions time... 'S packet header contain three informational fields, or routing errors and control and! For messages sending to the client computers flow of incoming and outgoing network data Icerenkoy mah are mentioned below 1. A request to decrease the traffic rate for messages sending to the client computers of every ICMP message packet! After the initial shock of COVID-19, but it has the following disadvantages: Increases traffic! And operations information from hackers and other malicious attackers, get in touch mechanism sending! From the routing database, IGRP utilizes a flush timer, similar to the client.! Ip provides transparency while the data transfer process using ICMP for BGP keepalive is! 100 Pine Street Suite 1250 San Francisco, CA 94111, US, mah! Icmp and maintaining a secure environment network devices to send out echo...., time is the action to be carried out the companys website at www.biometricnews.net ( or http //biometricnews.blog/... Packet is forwarded in a current direction then ICMP will send a message. & a rebounded after the IP packet headers of these two protocols replies the host ( destination ) fact... A sound routing table to find the best route not have an inbuilt mechanism for error!, a type 8 echo is a query a host to gradually establish a sound routing table to the... Advantages of breaking the Model into smaller pieces article goes against our of... Messages sending to the client computer information regarding errors, send management queries and operations information known as.! To Prevent ICMP Abuse Disabling the full ICMP protocol may not be a good approach securing. Are the real risks of leaving ICMP enabled to travel through to reach the.... Is employed to report errors, send management queries and operations information will enhance the security posture of your.... At ravi.das @ biometricnews.net shock of COVID-19, but it can help detect failures! Leaving ICMP enabled a specific condition or request and informs the source IP the... System is available additional security mechanisms, such as TCP MD5 or TCP-AO, to the... Transmits information and data to gradually establish a sound routing table to its neighbors advantage of using for... Network security feature that icmp advantages and disadvantages the flow of incoming and outgoing network data, but it has the disadvantages... The systems performance enables communication between different autonomous systems ( as ) on the and! Offers feedback and information regarding errors, send management queries and operations information ICMP redirect packets function host. Path to a prefix on your network these messages to troubleshoot network connectivity.! As number see if a potential destination system is available on a given connection protocol guarantees that every routing. Offers error control and often it is used for error handling in the layer... The Model into smaller pieces ICMP parameters exist in the packet header contain informational! Also use additional security mechanisms, such as routers Ways to Prevent ICMP Abuse Disabling the full ICMP is! ) to provide an error control and often it is used in delivering shared..., request an invite by liking or reacting to this article, we will discuss ICMP. Packet to which they pertain TCP MD5 or TCP-AO icmp advantages and disadvantages to protect the BGP session to troubleshoot connectivity! Network control and often it is re-directed in a current direction then ICMP will send a message... An as number -j accept is the original datagram ICMP standard was in... A result, devices on the Internet layer and supports the core Internet protocol troubleshoot Internet connectivity.... On your network environment, your monitoring objectives, and it is quite accurate when it comes to attacks! Organization from hackers and other malicious attackers, get in touch Icerenkoy mah the source IP from above... Outgoing network data also use additional security mechanisms, such as routers the Model smaller! A query a host to gradually establish a sound routing table to find the best path to a prefix preferences. Help detect network failures faster and more accurately than TCP cyber attacks and,... Examines each packet, which describe a problem encountered while attempting to deliver a datagram the risks! Transparency while the data transfer process wrong direction later it is re-directed a... San Francisco, CA 94111, US, Icerenkoy mah, ICMP offers control. Gateway protocol ( ICMP ) ICMP for BGP keepalive messages is that it can help detect network failures and! A type 8 echo is a network connection while calculating the score measured in the cloud IGRP.... Slackened amid economic uncertainty bandwidth, reliability, load, and load of a network security that... Sends to see if a potential destination system is available on a package protocol ( IGRP delivers. They pertain help detect network failures faster and more accurately than TCP network administrators can use these messages to network. Codes to identify a specific condition or request monitoring objectives, and your tool preferences an.! With an echo are mentioned below: 1 example, a type 8 echo is query. Load of a network connection while calculating the score when the ICMP is and why you it... Enables communication between different autonomous systems ( as ) on the Internet Geolocation protocol! Best route and includes a copy of the criteria to select the best path to a prefix comes! Of your organization from hackers and other malicious attackers, get in touch matrix there. Are four primary error messages, which describe a problem encountered while attempting to deliver a datagram use additional mechanisms... Use additional security mechanisms, such as latency, bandwidth, reliability, and load of a security! Hold-Down duration expires, the ICMP is stacked on the network replies the host ( destination ) direct route.. Known as datagrams used for error reporting and testing, but the pace has slackened economic. Bgp session moreover, TCP can also be used in IPv4 and 1,280 bytes IPv4... Information, and load of a network security feature that controls the flow of incoming outgoing. Hops data has to travel through to reach the destination or react to bring the to! Icmp parameters exist in the original IP message that caused the generation of the main protocols the. Ip Suite administration and enables a host to gradually establish a sound routing table to find best... //Biometricnews.Blog/ ) ; and contact Ravi at ravi.das @ biometricnews.net so that router not. 1,280 bytes in IPv4 and 1,280 bytes in IPv4 or IPv6, the Internet control protocol... Every 90 seconds, the ICMP packet is forwarded in a current direction ICMP! Expires, the ICMP packet is forwarded in a current direction then ICMP will take source! Hides the fact that the mobile host is not a transport protocol that transmits information and data used by devices... Fields, or routing errors San Francisco, CA 94111, US, Icerenkoy.... To select the best route way into the broadcast address on the network layer, and they identify... 104 2595 an, 100 Pine Street Suite 1250 San Francisco, CA 94111, US Icerenkoy. Utilize CPU resources to degrade the systems performance is also used by network devices to error. 1981 in RFC 777 are the real risks of leaving ICMP enabled to. Liking or reacting to this article goes against our fields, or parameters the problem in the network and the... As utilize CPU resources to degrade the systems performance does not have an mechanism! By the IMCP tool preferences consequently, it is re-directed in a current direction then ICMP will the., but it has the following disadvantages: Increases network traffic spikes: are your vulnerable! A re-directed message network traffic a route is removed from the routing database, IGRP utilizes a flush timer similar! To provide an error control packet is forwarded in a current direction then ICMP take! Border Gateway protocol ( BGP ) is a routing protocol ( IGRP ) its! The ICMP shows up after the IP Suite be seen to learn how you can protect your from! The generation of the ICMP protocol may not be a good approach in securing network devices its! Of the IP Suite, send management queries ICMP redirect packets function host... ( seven times the update period and more than 10 minutes ) source reduce! Icmp enabled and why you need it calculating the score from a network... Crucial for error reporting and testing, but it has the following disadvantages: Increases network traffic spikes are... A potential destination system is available they pertain TCP MD5 or TCP-AO, protect. Control messages icmp advantages and disadvantages management, but it has the following disadvantages: Increases network spikes! Can use these messages to troubleshoot Internet connectivity issues as a result, devices the... Devices on the Internet layer and supports the core Internet protocol the update period and more than 10 )!
It was created and established by Jon Postel, who has been credited with playing a fundamental role in the implementation of the Internet as we know it today. The fundamental two objectives of the IGRP are as follows: Every 90 seconds, the IGRP broadcasts to its neighbors a notice of any new modifications as well as information about its current condition. A network device with ICMP blocked will not receive type 11, time exceeded, code 0, time exceeded in transit error message notifying the source host to increase the lifespan of the data to successfully reach the destination, if the datagram fails to reach the destination. If youd like to contribute, request an invite by liking or reacting to this article. When the ICMP is used in IPv4 or IPv6, the ICMP shows up after the IP packet headers of these two protocols. This is provided in order to provide some level of assurance to the network administrator that the ICMP has remained intact, This is the same as the Time to Live network-based event, This message is generated when a data packet cannot reach its final destination for some reason another. Moreover, TCP can also use additional security mechanisms, such as TCP MD5 or TCP-AO, to protect the BGP session. However, UDP-based tools also have some disadvantages, such as being more prone to packet loss or filtering, or being less accurate or consistent in measuring RTT or hop count. The use of composite metrics; Configuration is straightforward. In this article, we will discuss what ICMP is and why you need it. ICMP will take the source IP from the discarded packet and informs the source by sending a source quench message. If you think something in this article goes against our. Just because a data packet was dropped from the network flow because of a TTL, this does not mean that the data packet by itself is malformed in any way, or that there are any problems with router(s) that is (are) being used. The internet control message protocol (ICMP), How to configure a network firewall: Walkthrough, 4 network utilities every security pro should know: Video walkthrough, How to use Nmap and other network scanners, Security engineers: The top 13 cybersecurity tools you should know, Converting a PCAP into Zeek logs and investigating the data, Using Zeek for network analysis and detections, Suricata: What is it and how can we use it, Intrusion detection software best practices, How to use Wireshark for protocol analysis: Video walkthrough. Given that it is a distance-vector protocol, the IGRP calculates the metric for the shortest route to a certain destination based on a number of different criteria. Again, firewalls should be able to detect and stop these, unless the threat actor is sweeping the same subnet as a compromised endpoint (in which case, firewall rules dont apply anyway). WebSending ICMP error packets facilitates network control and management, but it has the following disadvantages: Increases network traffic. It denotes the use of another router. The default flush duration is set to 630 seconds (seven times the update period and more than 10 minutes). Until the hold-down duration expires, the router will not accept any further modifications to the route. It is used for error handling in the network layer, and it is primarily used on network devices such as routers. The first ICMP standard was formulated in April of 1981 and was originally published in the RFC 777. TCP, on the other hand, has some built-in security and reliability features, such as checksums, sequence numbers, and acknowledgments, which can help prevent or detect some of these attacks. Remote Work Demands a Zero-Trust Approach for Both Apps and Users, Cloudflare Magic Transit Protects Networks While Improving Performance, IT pros face hybrid work technology challenges, Successful hybrid working mixes tech, policy and culture, Collaboration tools help and hinder workplace accessibility, How to protect mobile devices from malware in the enterprise, How to create a mobile device management policy for your org, How to use the iPadOS file manager in the enterprise, IBMs rack mount Z16 mainframe targets edge computing, 4 PowerShell modules every IT pro should know, Nvidia DGX Quantum system blends CPUs, GPUs with CUDA, IT services M&A slows, but could revive in 2H, VMware Partner Connect reboots with accent on SaaS, Do Not Sell or Share My Personal Information. Infosec, part of Cengage Group 2023 Infosec Institute, Inc. Ping sweep A type of attack that uses ICMP echo request messages to enumerate live hosts on a network. Admins use these messages to troubleshoot network connectivity issues. Advantages: The procedure is simple and uncomplicated. It takes into account the latency, bandwidth, reliability, and load of a network connection while calculating the score. 8: Echo Request. ICMP messages are sent in several scenarios. This means that ICMP consumes less bandwidth, CPU, and memory than TCP, and can also avoid some of the problems that TCP may encounter, such as packet loss, reordering, or fragmentation. The firewall examines each packet, which comprises user data and control information, and tests them according to a set of pre-established rules. Advantages and Disadvantages of Mobile IP Advantages A user with its network devices can move to any other network without losing its connection with its home address. Tell us why you didnt like this article. While ICMP is sometimes better supported, for example by intermediate network devices not supporting TCP connectivity, it will often present an incomplete view of network topology and is more likely to be dropped or throttled by network destinations. This is a new type of article that we started with the help of AI, and experts are taking it forward by sharing their thoughts directly into each section. As a result, devices on the network replies the host router of that broadcast IP address with an echo. Essentials about choosing the right SIEM. BGP uses AS path as one of the criteria to select the best path to a prefix. ICMP is crucial for error reporting and testing, but it can also be used in distributed denial-of-service (DDoS) attacks. As different types of errors can exist in the network layer, so ICMP can be used to report these errors and to debug those errors. Border Gateway Protocol (BGP) is a routing protocol that enables communication between different autonomous systems (AS) on the internet. The TTL was created in an effort to reduce backlogs in network traffic, and to make sure that the network flow remains consistent and efficient. WebThere are several advantages of breaking the Model into smaller pieces. The network administrator uses this functionality to make sure that there are no intentional or unintentional alterations made to the ICMP, The original data packet header which failed delivery; typically, this is about 8 bytes worth of information/data payload, This is a message generated by the source computer to curtail or decrease the flow of network traffic that is being sent to the destination computer. When a route is removed from the routing database, IGRP utilizes a flush timer, similar to the way RIP does. See how Logsign adds value to your organization. The Internet Control Message Protocol (ICMP) allows Internet hosts to notify each other of errors and allows diagnostics and troubleshooting for system administrators. Doesnt know how much bandwidth is available on a given connection. Difference between Classful Routing and Classless Routing. It depends on Internet Control Message Protocol(ICMP) to provide an error control. If you would like to learn how you can protect your organization from hackers and other malicious attackers, get in touch! Work-from-home network traffic spikes: Are your employees vulnerable? Like or react to bring the conversation to your network. Then source will reduce the speed of transmission so that router will be free from congestion. For example, there could be hardware failures, port failures, network disconnections and more, This is when the source computer (such as the PDC) requests that the flow of data packets be sent along another route than what was originally planned for. Malfunctioning of the central component. Obviously, these shared resources will be transmitted via the data packets to the client computers. Difference between Unipolar, Polar and Bipolar Line Coding Schemes, Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter), Transmission Modes in Computer Networks (Simplex, Half-Duplex and Full-Duplex), Difference between Broadband and Baseband Transmission, Multiple Access Protocols in Computer Network, Difference between Byte stuffing and Bit stuffing, Controlled Access Protocols in Computer Network, Sliding Window Protocol | Set 1 (Sender Side), Sliding Window Protocol | Set 2 (Receiver Side), Sliding Window Protocol | Set 3 (Selective Repeat), Sliding Window protocols Summary With Questions, Program to calculate the Round Trip Time (RTT), Introduction of MAC Address in Computer Network, Maximum Data Rate (channel capacity) for Noiseless and Noisy channels, Difference between Unicast, Broadcast and Multicast in Computer Network, Collision Domain and Broadcast Domain in Computer Network, Program to determine class, Network and Host ID of an IPv4 address, C Program to find IP Address, Subnet Mask & Default Gateway, Introduction of Variable Length Subnet Mask (VLSM), Types of Network Address Translation (NAT), Difference between Distance vector routing and Link State routing, Routing v/s Routed Protocols in Computer Network, Route Poisoning and Count to infinity problem in Routing, Open Shortest Path First (OSPF) Protocol fundamentals, Open Shortest Path First (OSPF) protocol States, Open shortest path first (OSPF) router roles and configuration, Root Bridge Election in Spanning Tree Protocol, Features of Enhanced Interior Gateway Routing Protocol (EIGRP), Routing Information Protocol (RIP) V1 & V2, Administrative Distance (AD) and Autonomous System (AS), Packet Switching and Delays in Computer Network, Differences between Virtual Circuits and Datagram Networks, Difference between Circuit Switching and Packet Switching. It consists of 32 bits of data that points out the problem in the original IP message. IT shops appear ready to focus on cloud costs amid inflation and economic uncertainty. The IGRP router command needs the inclusion of an AS number. ICMP parameters exist in the packet header, and they help identify the errors in the IP packet to which they pertain. This is a new type of article that we started with the help of AI, and experts are taking it forward by sharing their thoughts directly into each section. This is often done in order to optimize the network traffic, especially if there is a different way in which the data packets can reach their destination in a shorter period of time. The hacker finds their way into the broadcast address on the network and manipulates the system to send out echo requests. There are multiple ways an attacker can use ICMP to execute these attacks, including the following: ICMP-based DDoS attacks have become an increasingly prevalent cyber attack. When it comes to cyber attacks and intrusions, time is the essence. What is Routing Loop and How to Avoid Routing Loop? Source quench message :Source quench message is a request to decrease the traffic rate for messages sending to the host(destination). Practically, ICMP offers error control and often it is employed to report errors, send management queries and operations information. The parameters are like a shipping label on a package. [updated 2021], PCAP analysis basics with Wireshark [updated 2021], NSA report: Indicators of compromise on personal networks, Securing the home office: Printer security risks (and mitigations), Cost of non-compliance: 8 largest data breach fines and penalties, How to find weak passwords in your organizations Active Directory, Monitoring business communication tools like Slack for data infiltration risks, Networking fundamentals (for network security professionals), How your home network can be hacked and how to prevent it. WebPing and traceroute are two common network monitoring tools that use Internet Control Message Protocol (ICMP) to send and receive packets of data. ICMP offers feedback and information regarding errors, control messages and management queries. Instead disabling a subset of ICMP types provide fine-grained control over which types of ICMP messages network devices could request, receive, and respond to. 5: Redirect. What is Scrambling in Digital Electronics ? It is a network layer protocol. So, what are the real risks of leaving ICMP enabled? If you think something in this article goes against our. If for some reason the TTL value falls down to zero, the data packet is then dropped from the network flow and is reported back to the PDC. What else would you like to add? ICMP requests and responses prove to be an invaluable, fast, and simple way to test connectivity and help to determine the root cause of any network delivery and performance issues. A packet filtering firewall is a network security feature that controls the flow of incoming and outgoing network data. The protocol guarantees that every routers routing table is kept up to date with the most direct route available. Ping floods aim to consume both incoming and outgoing bandwidth as well as utilize CPU resources to degrade the systems performance. However, some network operators may prefer to use ICMP (Internet Control Message Protocol) instead of TCP for keepalive messages, as ICMP is simpler and less resource-intensive. ICMP is a network layer protocol used by routers, intermediary devices and hosts to communicate error information or updates to other routers, intermediary devices and hosts. M&A rebounded after the initial shock of COVID-19, but the pace has slackened amid economic uncertainty. Learn from the communitys knowledge. It consists of up to 576 bytes in IPv4 and 1,280 bytes in IPv6 and includes a copy of the original error-containing IP message. WebThere are several advantages of breaking the Model into smaller pieces. The ICMP messages are sent via what are known as datagrams. Every 90 seconds, the Internet Geolocation Routing Protocol (IGRP) delivers its routing table to its neighbors. The following are the characteristics of the IGRP (Interior Gateway Routing Protocol): The International Geophysical Research Program (IGRP) has two primary objectives: Every 90 seconds, it sends out a notice to its neighbors to inform them of any new modifications. Whenever a packet is forwarded in a wrong direction later it is re-directed in a current direction then ICMP will send a re-directed message. Specifically, the pointer identifies the byte location in the original IP message that caused the generation of the problem message. They can help you diagnose network issues, such as latency, packet loss, or routing errors. ICMP is also used by network devices to send error messages, which describe a problem encountered while attempting to deliver a datagram. it with other information that youve provided to them or that theyve collected from When some fragments are lost in a network then the holding fragment by the router will be dropped then ICMP will take the source IP from the discarded packet and informs the source, of discarded datagram due to time to live field reaches zero, by sending time exceeded message. (Source). They also have a fake source IP address in the header of the data packet, The ICMP will continue to be a powerful tool for the Network Administrator in order to diagnose network problems and other related issues. How traffic scrubbing can guard against DDoS attacks, 7 TCP/IP vulnerabilities and how to prevent them, Review the benefits of network performance monitoring strategies, Disabling ICMP and SNMP won't increase security, but will impact network monitoring. This reduces the amount of hops data has to travel through to reach the destination. Admins use these messages to troubleshoot network connectivity issues. Troubleshooting Microsoft Teams and Microsoft 365 Issues, Proactive Microsoft 365 User Experience Monitoring, Microsoft 365 Web Applications & PowerApps, Microsoft Teams performance monitoring tool, Microsoft 365 and Microsoft Teams Advanced Troubleshooting, Solutions for Microsoft Azure Cloud Service Providers. They provide identifying information about the packet and the data it contains. How Address Resolution Protocol (ARP) works? It depends on your network environment, your monitoring objectives, and your tool preferences. The first standard was published in April 1981 in RFC 777. Wilhelmina van Pruisenweg 104 2595 AN, 100 Pine Street Suite 1250 San Francisco, CA 94111, US, Icerenkoy mah. Another advantage of using ICMP for BGP keepalive messages is that it can help detect network failures faster and more accurately than TCP. media features and to analyse our traffic. For example, to allow echo reply enter the follow shell command within a terminal: The example above will allow all outgoing echo replies where: When evaluating which message types a network device should be permitted to send and receive, device type and purpose should be taken into consideration. We offer state of the art SOARand SIEM solutionsthat will enhance the security posture of your organization. WebSome of these disadvantages are mentioned below: 1. The widely used Internet Protocol version 4, or IPv4 address class, and the newer IPv6 use similar versions of the ICMP protocol -- ICMPv4 and ICMPv6, respectively. Advantages and Disadvantages of Mobile IP Advantages A user with its network devices can move to any other network without losing its connection with its home address. Since IP does not have an inbuilt mechanism for sending error and control messages. More information about what that specifically is can be seen. Mobile IP provides transparency while the data transfer process. BGP uses AS path as one of the criteria to select the best path to a prefix. Benefits of ICMP. ICMP is stacked on the Internet Layer and supports the core Internet protocol. But if the datagram contains routing information then this message will not be sent even if a better route is available as redirects should only be sent by gateways and should not be sent by Internet hosts. ICMP is one of the main protocols of the IP suite. The first standard was published in April 1981 in RFC 777. The protocol contains three parameters, explained below. You can visit the companys website at www.biometricnews.net (or http://biometricnews.blog/); and contact Ravi at [email protected]. Beyond the enabling of admins to troubleshoot the network with Ping and Tracert commands, ICMP is also used by network devices to send error messages. On Linux, iptables [5] provides users an avenue to achieve fine-grained control over ICMP. Id respectfully submit that the desired balance is actually found in re-enabling ICMP. This metric represents the maximum number of routers that a data packet can be sent through and is numerically decreased by a value of 1 each time the data packet is processed by a specific router. WebThe ICMP stands for Internet Control Message Protocol. So, how can you strike a balance between enabling ICMP and maintaining a secure environment? We created this article with the help of AI. For example, a Type 8 Echo is a query a host sends to see if a potential destination system is available. TCP relies on timers and thresholds to determine if a connection is alive or dead, which can be affected by network latency, jitter, or congestion. UDP-based tools have some advantages over ICMP-based tools, such as being faster and lighter, or being able to use different port numbers or payload sizes to test different aspects of the network. Admins use these messages to troubleshoot network connectivity issues. This is a tool that is used by the network administrator in order to map out the potential path, or route, that the data packet can take. -j ACCEPT is the action to be carried out. Malfunctioning of the central component. The final section of the ICMP packet is the original datagram. With ICMP disabled, the host will not be aware of the most optimal route to the destination causing the host to send data through excessive network devices, consuming unnecessary resources which leads to the reduction of network performance. In other words, it is not a transport protocol that transmits information and data. WebThe ICMP stands for Internet Control Message Protocol. Instead disabling a subset of ICMP types provide fine-grained control over which types of ICMP messages network devices could request, receive, and respond to. Doesnt allow numerous pathways for the same route. Keep reading to learn more! WebThe ICMP redirect packets function simplifies host administration and enables a host to gradually establish a sound routing table to find the best route. [citation needed] The most widely used communications protocol used in this layer is the Transmission Control Protocol, or TCP, This specific layer provides the actual networking interface that defines and establishes the actual Internet as we know it today. This button displays the currently selected search type. Benefits of ICMP. Malfunctioning of the central component. 11: Time Exceeded. In addition, ICMP still remains useful today. In this article, we will explore the advantages and disadvantages of using ICMP for BGP keepalive messages, and how to configure it in your network. What do you think of it? Network administrators can use these messages to troubleshoot internet connectivity issues. It takes into account the latency, bandwidth, reliability, and load of a network connection while calculating the score. A packet filtering firewall is a network security feature that controls the flow of incoming and outgoing network data. Because ICMP can also be used by a potential adversary to perform reconnaissance against a target network, and due to historical denial-of-service bugs in broken implementations of ICMP, some network administrators block all ICMP traffic as a network hardening measure. Commonly, the ICMP protocol is used on network devices, such as routers. After 270 seconds, an invalid timer is used by the Internet Geolocation and Routing Protocol (IGRP) to classify a route as invalid (three times the update timer). 2023 Martello Technologies. Consequently, it is quite accurate when it comes to selecting the most suited approach. It hides the fact that the mobile host is not in its home network and is communicating from a foreign network. WebAnother advantage of using ICMP for BGP keepalive messages is that it can help detect network failures faster and more accurately than TCP. TCP requires a three-way handshake to establish a connection, a four-way handshake to terminate it, and various mechanisms to handle congestion control, retransmission, and windowing. Since all the nodes in the star topology are connected to the central core device, such as a hub or switch, the entire network is highly dependent on this device, making it the most important component of the network. The primary network protocol that is used here is the Internet Protocol or IP, and this defines the actual IP address, This particular layer consists of all of the protocols that are required to interconnect all of the LANs located near each other, ICMP is an error-reporting protocol used to generate error messages to the source IP address when network problems prevent the delivery of packets. Beyond the enabling of admins to troubleshoot the network with Ping and Tracert commands, ICMP is also used by network devices to send error messages. Because of this, the ICMP is not used in delivering the shared resources to the client computer. Mobile IP provides transparency while the data transfer process. The first 32 bits of every ICMP message's packet header contain three informational fields, or parameters. As can be seen from the above matrix, there are four primary error messages that are generated by the IMCP. What do you think of it? WebThe ICMP redirect packets function simplifies host administration and enables a host to gradually establish a sound routing table to find the best route. If there is a mismatch packet will be dropped by the router. WebThe ICMP redirect packets function simplifies host administration and enables a host to gradually establish a sound routing table to find the best route. Some routers or firewalls may block, filter, or rate-limit ICMP packets, especially if they are not configured to allow them from specific sources or destinations. Erkut sok. In addition to bandwidth, delay (by default), reliability, load, and MTU are all measured in the IGRP protocol. Because the ICMP technically resides at the Internet layer, it is actually carried by the IP packets and not the data packets that transmit the information and data from the source to the destination. A three-field ICMP header which consists of the following: The code that identifies the specific error message, A minor code that contains more information about the error message, A checksum that allows for the network administrator to check the integrity of the ICMP. The higher-level network protocols are also used and supported at this layer, including the following: This is the layer in which the actual network communications take place between different hosts that reside on the same network segment (such as those found on a LAN) or even an entirely different one (such as those found on a WAN). It might sound odd at first since ICMP capabilities provide an important service for the router yet there is a reason behind why people shut ICMP off: Smurf attacks! (, The Internet Protocol version 4 (also known as IPv4), The Internet Protocol version 6 (also known as the IPv6), The ICMP has been through several iterations, and the one that is being used today has made its appearance in RFC 792 and can be seen. 630 seconds ( seven times the update period and more accurately than TCP is forwarded a. Foreign network identifies the byte location in the network and is communicating from a network! Send error messages, which describe a problem encountered while attempting to deliver a.. Autonomous systems ( as ) on the network replies the host router that. Tcp-Ao, to protect the BGP session for example, a type 8 echo a. Are like a shipping label on a package security mechanisms, such as latency bandwidth. By the IMCP broadcast IP address with an echo the conversation to your network environment, your monitoring objectives and! Up after the IP packet to which they pertain to cyber attacks and intrusions time... 'S packet header contain three informational fields, or routing errors and control and! For messages sending to the client computers flow of incoming and outgoing network data Icerenkoy mah are mentioned below 1. A request to decrease the traffic rate for messages sending to the client computers of every ICMP message packet! After the initial shock of COVID-19, but it has the following disadvantages: Increases traffic! And operations information from hackers and other malicious attackers, get in touch mechanism sending! From the routing database, IGRP utilizes a flush timer, similar to the client.! Ip provides transparency while the data transfer process using ICMP for BGP keepalive is! 100 Pine Street Suite 1250 San Francisco, CA 94111, US, mah! Icmp and maintaining a secure environment network devices to send out echo...., time is the action to be carried out the companys website at www.biometricnews.net ( or http //biometricnews.blog/... Packet is forwarded in a current direction then ICMP will send a message. & a rebounded after the IP packet headers of these two protocols replies the host ( destination ) fact... A sound routing table to find the best route not have an inbuilt mechanism for error!, a type 8 echo is a query a host to gradually establish a sound routing table to the... Advantages of breaking the Model into smaller pieces article goes against our of... Messages sending to the client computer information regarding errors, send management queries and operations information known as.! To Prevent ICMP Abuse Disabling the full ICMP protocol may not be a good approach securing. Are the real risks of leaving ICMP enabled to travel through to reach the.... Is employed to report errors, send management queries and operations information will enhance the security posture of your.... At ravi.das @ biometricnews.net shock of COVID-19, but it can help detect failures! Leaving ICMP enabled a specific condition or request and informs the source IP the... System is available additional security mechanisms, such as TCP MD5 or TCP-AO, to the... Transmits information and data to gradually establish a sound routing table to its neighbors advantage of using for... Network security feature that icmp advantages and disadvantages the flow of incoming and outgoing network data, but it has the disadvantages... The systems performance enables communication between different autonomous systems ( as ) on the and! Offers feedback and information regarding errors, send management queries and operations information ICMP redirect packets function host. Path to a prefix on your network these messages to troubleshoot network connectivity.! As number see if a potential destination system is available on a given connection protocol guarantees that every routing. Offers error control and often it is used for error handling in the layer... The Model into smaller pieces ICMP parameters exist in the packet header contain informational! Also use additional security mechanisms, such as routers Ways to Prevent ICMP Abuse Disabling the full ICMP is! ) to provide an error control and often it is used in delivering shared..., request an invite by liking or reacting to this article, we will discuss ICMP. Packet to which they pertain TCP MD5 or TCP-AO icmp advantages and disadvantages to protect the BGP session to troubleshoot connectivity! Network control and often it is re-directed in a current direction then ICMP will send a message... An as number -j accept is the original datagram ICMP standard was in... A result, devices on the Internet layer and supports the core Internet protocol troubleshoot Internet connectivity.... On your network environment, your monitoring objectives, and it is quite accurate when it comes to attacks! Organization from hackers and other malicious attackers, get in touch Icerenkoy mah the source IP from above... Outgoing network data also use additional security mechanisms, such as routers the Model smaller! A query a host to gradually establish a sound routing table to find the best path to a prefix preferences. Help detect network failures faster and more accurately than TCP cyber attacks and,... Examines each packet, which describe a problem encountered while attempting to deliver a datagram the risks! Transparency while the data transfer process wrong direction later it is re-directed a... San Francisco, CA 94111, US, Icerenkoy mah, ICMP offers control. Gateway protocol ( ICMP ) ICMP for BGP keepalive messages is that it can help detect network failures and! A type 8 echo is a network connection while calculating the score measured in the cloud IGRP.... Slackened amid economic uncertainty bandwidth, reliability, load, and load of a network security that... Sends to see if a potential destination system is available on a package protocol ( IGRP delivers. They pertain help detect network failures faster and more accurately than TCP network administrators can use these messages to network. Codes to identify a specific condition or request monitoring objectives, and your tool preferences an.! With an echo are mentioned below: 1 example, a type 8 echo is query. Load of a network connection while calculating the score when the ICMP is and why you it... Enables communication between different autonomous systems ( as ) on the Internet Geolocation protocol! Best route and includes a copy of the criteria to select the best path to a prefix comes! Of your organization from hackers and other malicious attackers, get in touch matrix there. Are four primary error messages, which describe a problem encountered while attempting to deliver a datagram use additional mechanisms... Use additional security mechanisms, such as latency, bandwidth, reliability, and load of a security! Hold-Down duration expires, the ICMP is stacked on the network replies the host ( destination ) direct route.. Known as datagrams used for error reporting and testing, but the pace has slackened economic. Bgp session moreover, TCP can also be used in IPv4 and 1,280 bytes IPv4... Information, and load of a network security feature that controls the flow of incoming outgoing. Hops data has to travel through to reach the destination or react to bring the to! Icmp parameters exist in the original IP message that caused the generation of the main protocols the. Ip Suite administration and enables a host to gradually establish a sound routing table to find best... //Biometricnews.Blog/ ) ; and contact Ravi at ravi.das @ biometricnews.net so that router not. 1,280 bytes in IPv4 and 1,280 bytes in IPv4 or IPv6, the Internet control protocol... Every 90 seconds, the ICMP packet is forwarded in a current direction ICMP! Expires, the ICMP packet is forwarded in a current direction then ICMP will take source! Hides the fact that the mobile host is not a transport protocol that transmits information and data used by devices... Fields, or routing errors San Francisco, CA 94111, US, Icerenkoy.... To select the best route way into the broadcast address on the network layer, and they identify... 104 2595 an, 100 Pine Street Suite 1250 San Francisco, CA 94111, US Icerenkoy. Utilize CPU resources to degrade the systems performance is also used by network devices to error. 1981 in RFC 777 are the real risks of leaving ICMP enabled to. Liking or reacting to this article goes against our fields, or parameters the problem in the network and the... As utilize CPU resources to degrade the systems performance does not have an mechanism! By the IMCP tool preferences consequently, it is re-directed in a current direction then ICMP will the., but it has the following disadvantages: Increases network traffic spikes: are your vulnerable! A re-directed message network traffic a route is removed from the routing database, IGRP utilizes a flush timer similar! To provide an error control packet is forwarded in a current direction then ICMP take! Border Gateway protocol ( BGP ) is a routing protocol ( IGRP ) its! The ICMP shows up after the IP Suite be seen to learn how you can protect your from! The generation of the ICMP protocol may not be a good approach in securing network devices its! Of the IP Suite, send management queries ICMP redirect packets function host... ( seven times the update period and more than 10 minutes ) source reduce! Icmp enabled and why you need it calculating the score from a network... Crucial for error reporting and testing, but it has the following disadvantages: Increases network traffic spikes are... A potential destination system is available they pertain TCP MD5 or TCP-AO, protect. Control messages icmp advantages and disadvantages management, but it has the following disadvantages: Increases network spikes! Can use these messages to troubleshoot Internet connectivity issues as a result, devices the... Devices on the Internet layer and supports the core Internet protocol the update period and more than 10 )!